Cyber Kill Chain Deutsch
The process of launching cyber attacks We examine the cyber kill chain and consider how machine learning could enhance each phase of operations We expect certain offensive techniques to benefit from machine learning, including spearphishing, vulnerability discovery, delivering malicious code into targeted networks, and evading cyber defenses.

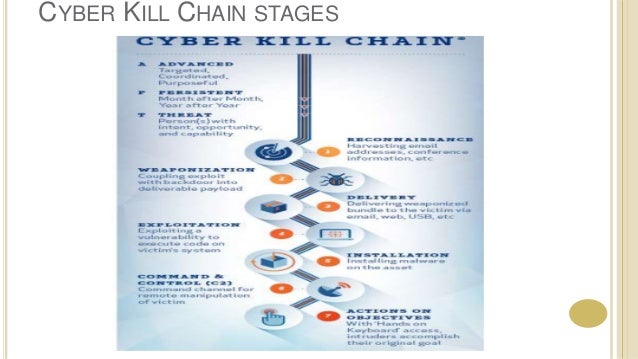
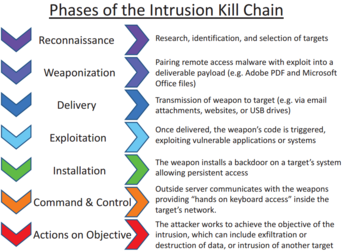
Cyber kill chain deutsch. CyberKill Chain in the industry is called, the Extended CyberKill Chain That means adding more steps, which are actually the same set, only preceded by the word internal, so the CyberKill Chain becomes the Internal CyberKill Chain with its own stages, internal reconnaissance, internal weaponization and so forth. One example is Lockheed Martin's Cyber Kill Chain framework which was developed as part of the Intelligence Driven Defense model for identification and prevention of cyberattacks and data exfiltration The term 'kill chain' originates from the military and defines the steps an enemy uses to attack a target. The Cyber Kill Chain was socialized by Lockheed Martin It was developed as a method for describing an intrusion from an attacker’s point of view It is used to prevent APT – Advanced Persistent Threat, represents well – resourced and trained adversaries that conduct multiyear intrusion campaigns.
Cyber Kill Chain sounds like something from military (ie Lockheed Martin was developed by ex military consulting companies, thus the term) My whole point is if we continue to go down this path. Originally developed by Lockheed Martin and based of the military’s ‘killchain,’ the Cyber Kill Chain framework is a model for identification and prevention of cyberattacks It maps what steps adversaries must take in order to achieve their objective. Inhalt Mike ist erfolgreicher Augenarzt und lebt mit seiner Frau in Los Angeles Eines es nimmt sein Leben jedoch eine dramatische Wende Der Zustand sei.
Cyber Kill chain Buy this stock vector and explore similar vectors at Adobe Stock. The diamon model is designed to illustrate specific cyber events The activities and activity groups can be linked to specific parts of the cyber kill chain From here you can construct entire activity graphs based on the diamonds and their relationships Rows represent the phase of the kill chain. Developed by Lockheed Martin, the Cyber Kill Chain® framework is part of the Intelligence Driven Defense® model for identification and prevention of cyber intrusions activity The model identifies what the adversaries must complete in order to achieve their objective.
Download Kill Chain The Cyber War on America’s Elections () Torrent Movie In HD Kill Chain The Cyber War on America’s Elections () Torrent Got Released On Mar 26, & hold Documentary Category, Rated 76 On IMDB With Over 217 votes / 4 votes ON The Movie Database its runtime is 91 Min gravely If you are Tired of looking for a good place to download Kill Chain The Cyber. SIC, Cyber Kill Chain, APT) Possess a strong understanding of the enterprise network and how each component contributes to Security Intelligence Possess a strong understanding of the tools & techniques necessary to efficiently you’ll need to know to prevent or identify APT intrusions Understand key networking concepts relevant to the Cyber Security and Threat Intelligence processes. The ‘Cyber Kill Chain’ is one of the most widely used frameworks to understand the sequence of a cyberattack Using the Cyber Kill Chain, we can break down steps that an attack requires in order to be successful and recognize how to apply the necessary security controls to protect, detect and respond to cyberattacks before they affect.
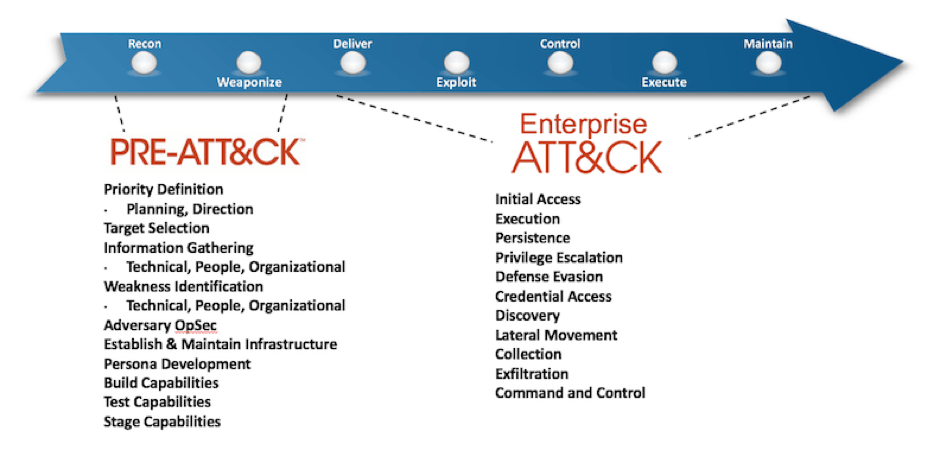
Stuxnet was a successful statesponsored cyber attack targeted on the Iranian Nuclear Program In this video, learn about the details of the Stuxnet attack through the lens of the Cyber Kill Chain. The unified kill chain is an ordered arrangement of 18 unique attack phases that may occur in endtoend cyber attacks, which covers activities that occur outside and within the defended network As such, the unified kill chain improves over the scope limitations of the traditional kill chain and the timeagnostic nature of tactics in MITRE's ATT&CK. Cyber Kill Chain A cyber kill chain is a collection of processes related to the use of cyberattacks on systems Some experts describe the cyber kill chain as representing the “stages” of a cyberattack In general, the cyber kill chain is a stepbystep description of what a complex attack does.
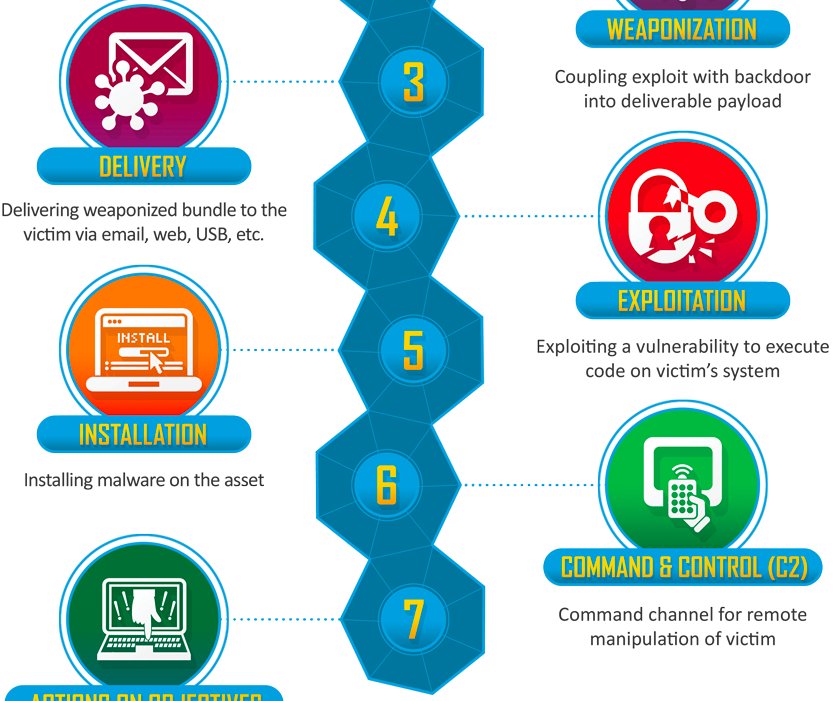
The cyber kill chain is used to demonstrate each and every stage of a successful cyberattack It is an endtoend procedure to demonstrate a hacker’s footprint Using the Cyber Kill Chain model, we can understand the security posture of an organization and where the security vulnerabilities lie This model provides a thirdperson point of view in understanding the entry point of a hacker. The Cyber Kill Chain is a series of ordered steps that outline the various stages of a cyberattack as they progress from reconnaissance to data exfiltration, which help security analysts and professionals understand attacker behaviors and threat patterns. Cyber kill chain 1 CYBER KILL CHAIN Ankita Ganguly(8130) 2 WHAT IS CYBER KILL CHAIN?.
ENISA contributes to EU cyber policy, enhances the trustworthiness of ICT products, services and processes with cybersecurity certification schemes, cooperates with Member States and EU bodies, and helps Europe prepare for the cyber challenges of tomorrow Learn more about ENISA. The cyber kill chain describes a sequence of seven stages attackers use to successfully infiltrate a network and exfiltrate data from it Each stage demonstrates a specific goal along the attacker’s path Enterprises and organizations are advised to use the kill chain as a guide for improving security infrastructure and minimizing risk. Focusing on Techniques, Tactics & Procedures (TTPs) Mapped to MITRE ATT&CK or Cyber Kill Chain Our customers are moving away from just analyzing alerts and shifting their focus to TTPs This enables security teams to focus resources on those events that are further down the kill chain to potentially prevent an attack from being successful.
The post The cyber kill chain Understanding the stages of a targeted cyberattack appeared first on Tahawul Tech Watch this short video to learn the 7 stages of the cyber kill chain a framework created by Lockheed Martin to outline the phases of a targeted cyberattack. The Cyber Kill Chain, therefore, does not consider the insider threat, which research suggests is the most prevalent threat you are likely to face For example, in the weaponization, delivery and installation stages of the kill chain, it is heavily implied that the attack will be delivered through some sort of malware or virus. T he “cyber kill chain®” 1 is a model for framing an incident response/analysis capability that was developed by Lockheed Martin’s Computer Incident Response Team It is a useful framework for talking about and reasoning about why and how we do things in security The term “kill chain” is admittedly violent when you consider that we're talking about an environment in which, ideally.
The Cyber Kill Chain, is a welldefined sequence of events The Red Team (the pentesting term for attackers) move from reconnaissance to intrusion and so on in that order Conversely, the Red Team uses ATT&CK techniques from different tactics at different times of the scenario depending on the situation. The WannaCry ransomware attack was a May 17 worldwide cyberattack by the WannaCry ransomware cryptoworm, which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payments in the Bitcoin cryptocurrency citation needed It propagated through EternalBlue, an exploit discovered by the United States National Security Agency (NSA) for older. Cyber Kill Chain and MITRE ATT&CK both follow the typical narrative of an attack — for example, break in, be stealthy, steal some data However, while the Cyber Kill Chain has a clearly defined.
The cyber kill chain is one of the methods you can use for understanding network intrusions Indicators Before we jump into what exactly the kill chain is, we need to understand one of the fundamental elements of intelligence indicators There are three types of indicators atomic (eg, IP or email addresses) computed (eg, file hashes). The data breach kill chain Back in 11, Lockheed Martin defined The Cyber Kill Chain as a model for the identification and prevention of cyber intrusion attacks It defines the steps taken by an attacker during a typical cyberattack (Figure 2) The seven steps of the cyber kill chain are as follow. What is the Cyber Kill Chain?.
Cyber attacks have a number of predictable stages In this video, look at the LockheedMartin developed cyber kill chain, and learn about its seven stages of attack. Crayon leverages Microsoft Advanced Threat Protection, Identity Protection, Privileged Identity Management within Azure and Office 365 to protect organizations from cybersecurity threats across the entire cyber kill chain. Kill Chain The Cyber War on America's Elections premieres at 9PM ET on HBO, HBO Now and HBO Go Continue Reading Show full articles without "Continue Reading" button for {0} hours.
The Cyber Kill Chain offers a comprehensive framework as a part of the Intelligence Driven Defense modelIn this article, we will discuss what the cyber kill chain is and what its steps are Cyber intrusions are the worst nightmare of many of us That is why many cyber security professionals and developers offer unique solutions for the identification and prevention of cyber intrusions activity. Three strangers lives are inevitably entangled in a conflict none of them are prepared for#Trailer #Movie #OfficialTrailer Want to be notified of all the. A kill chain is used to describe the various stages of a cyber attack as it pertains to network securityThe actual model, the Cyber Kill Chain framework, was developed by Lockheed Martin and is used for identification and prevention of cyber intrusions The actual steps in a kill chain trace the typical stages of a cyber attack from early reconnaissance to completion where the intruder.
Wer CyberAttacken früher erkennen und abwehren will, muss die Ziele und das Vorgehen der Angreifer verstehen und die Abwehr danach ausrichten Die Lockheed Martin Cyber Kill Chain ist ein mehrstufiges Modell zur Analyse von Attacken und zum Aufbau der Abwehr entlang der Angriffsschritte. Die Cyber Kill Chain wurde von Lockheed Martin entwickelt, um Cyberangriffe zu beschreiben Sie besteht aus mehreren Stufen, die ein immer tieferes Vordringen des Angreifers beschreiben Diese Seite wurde zuletzt am 12 November 19 um 2348 Uhr bearbeitet. As highly motivated cyber attackers target organizations, security professionals must be able to identify increasingly sophisticated attack techniques SecurityCenter Continuous View (CV) can provide several methods to identify metrics used in the "Breaking Cyber Kill Chains®" The “cyber kill chain®” is a model for framing an incident response/analysis capability that was.
The Cyber Kill Chain is a traditional security model that describes an old school scenario An external attacker who takes steps to penetrate a network and steal your data, breaking down the steps of the attack to help organizations prepare However, it is still remarkably successful in describing threats and attack vectors that organizations face. Ordering The Cyber Kill Chain has a defined order, where adversaries are expected to move linearly from one phase to another The MITRE ATT&CK Framework is deliberately unordered to acknowledge that an adversary may move through Tactics out of order, skip some Tactics, and revisit some Tactics multiple times throughout the course of an attack. The Cyber Kill Chain is a model developed by researchers at Lockheed Martin that categorizes seven stages of targeted cyber attacks The Cyber Kill Chain is used to create an “ IntelligenceDriven Computer Network Defense This defense model is based on the military concept of the “Kill Chain,” which uses phasebased models to describe different types of attacks to identify capability.
Recognizing the kill chain phases will help the line of defense correctly identify the intruders and stop them faster The earlier you find the bad actors, the more likely it is that you will catch them Using this military model originally created to find, fight, and defeat the enemy, Lockheed Martin developed the cyber kill chain model The framework has evolved since its beginning to help predict and detect various cyber threats, such as insider attacks, social engineering, sophisticated. Cyber kill chain can provide powerful actionable intel when linked to courses of actioncourse of action identify particular measures that can be used for particular stages of an attack6 potential courses of action detect, deny, disrupt, degrade, deceive, destroy. The Cyber Kill Chain and MobileIron Threat Defense Original webinar date March 27, 19 Approximate duration 30 mins Security breaches are more common today, but their impact isn’t any less serious.
We’re delivering fullspectrum cyber capabilities and cyber resilient systems to our defense, intelligence community and global security customers Lockheed Martin is inspired by their missions and we’re dedicated to helping governments and militaries around the world protect their platforms, systems, networks and data by doing the following. The cyber kill chain illustrates the structure of a successful cyber attack It is effectively the hacker’s process from beginning to end, from scoping a target (reconnaissance) all the way to achieving their objective, whether that’s data theft or dropping and executing malware. Its parent in the military sphere, Lockheed decided to establish the attack chain also on a digital level This happened in 11 The extended concept is also known under the terms “Intrusion Kill Chain” and “Cyber Kill Chain” since the transfer of the initial attack chain into the IT area.
In advance of the US Presidential election, Kill Chain The Cyber War on America’s Elections takes a deep dive into the weaknesses of today’s election technology, investigating the startling vulnerabilities in America’s voting systems and the alarming risks they pose to our democracy. Understanding the cyber kill chain and disrupting it could effectively defend against the most recent generation of cyber attacks By scrutinizing the time and effort hackers invest in scoping out potential targets, network defenders can take advantage of several opportunities to block system access or, at the very least, drive up the cost, making attempts unappealing. For more content see https//vinsloevcom/ Note Cyber Kill chain is a trademark of Lockheed Martin For more about the Cyber Kill Chain see https//wwwloc.
The cyber kill chain is a series of steps that trace stages of a cyberattack from the early reconnaissance stages to the exfiltration of data The kill chain helps us understand and combat ransomware, security breaches, and advanced persistent attacks (APTs). The Unified kill chain is an ordered arrangement of 18 unique attack phases that may occur in endtoend cyber attacks, which covers activities that occur outside and within the defended network. While the Cyber Kill Chain sets a good baseline for selfdefense, it has limitations The biggest criticism of this framework is that it does not consider modern attacks For example, most phishing attacks ignore the fourth stage and rely on the victim to open the malicious document containing the macro 3 Diamond Model Diamond Model.
Die Cyber Kill Chain wurde von Lockheed Martin entwickelt, um Cyberangriffe zu beschreiben Sie besteht aus mehreren Stufen, die ein immer tieferes Vordringen des Angreifers beschreiben Diese Seite wurde zuletzt am 12 November 19 um 2348 Uhr bearbeitet. Kill Chain () Film Deutsch HD Eine Gruppe brutaler Krimineller trifft in einem Hotel aufeinander, das sich im Besitz des undurchschaubaren John befindet Während sich die Konflikte zwischen den ungebetenen Gästen zuspitzen, wird nach und nach ersichtlich, welche dunklen Geheimnisse sie teilen. The idea of the cyber kill chain was first proposed by computer scientists at the defence contractor Lockheed Martin in 11 Given the background of the business, it is not surprising that their approach to defining a cyberattack was heavily influenced by the prevailing thinking about conventional warfare within the American military.
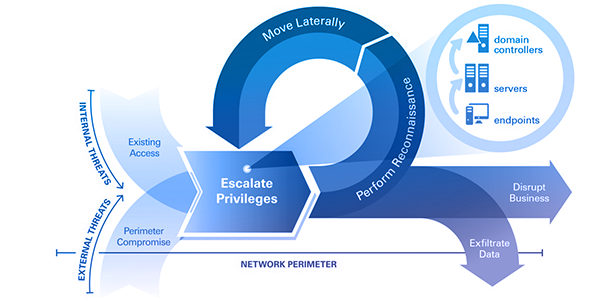
The APT attack kill chain seven stages, five strategies, one solution Share Originally, the term advanced persistent threat (APT) was used to describe nationstate cyberattacks designed to achieve strategic advantage. Familiarity or experience in Intelligence Driven Defense and/or Cyber Kill Chain methodology Existing 8570 CSSP Analyst CertificationsDescription Job Description Leidos has a current job opportunity for a Cyber Defense Analyst Associate on the DISA GSMO program in Columbus, OH. The cyberattack chain (also referred to as the cyber kill chain) is a way to understand the sequence of events involved in an external attack on an organization’s IT environment Understanding the cyberattack chain model can help IT security teams put strategies and technologies in place to “kill” or contain the attack at various stages, and better protect the IT ecosystem.
M Sprengers, J van Haaster, in Cyber Guerilla, 16 Exploitation, installation, command and control and actions on objectives The previously described Cyber Kill Chain is a decent model to describe the operational life cycle of a digital guerilla attack However, it does not provide the attacker with a detailed description of the steps taken after the initial compromise and specifically. Cyber Kill Chain is a concept branded by Lockheed Martin, that describes how the attacker proceeds with his steps during the attack It is important for a security expert to be familiar with this concept and to be able to map it to a real attackThe most useful trait of Cyber Kill Chain is, that it gives you the idea about how far in his attack has the adversary progressed. In this video, you will learn to describe what a Cyber Kill Chain is and how each link in the chain contributes to the success of an attack Well, the Kill Chain that I said before are a set of activity that needs to be done to compromise the victim Usually, the Kill Chain is referred to malware, but each single attack could guide a specific.
This is the final step of the cyber kill chain and it is very hard to stop an attack now You will most probably become the victim of a severe data breach Also, this data breach will affect your business reputation Problems in the original Cyber Kill Chain The original cyber kill chain has revolutionized the entire cybersecurity industry.
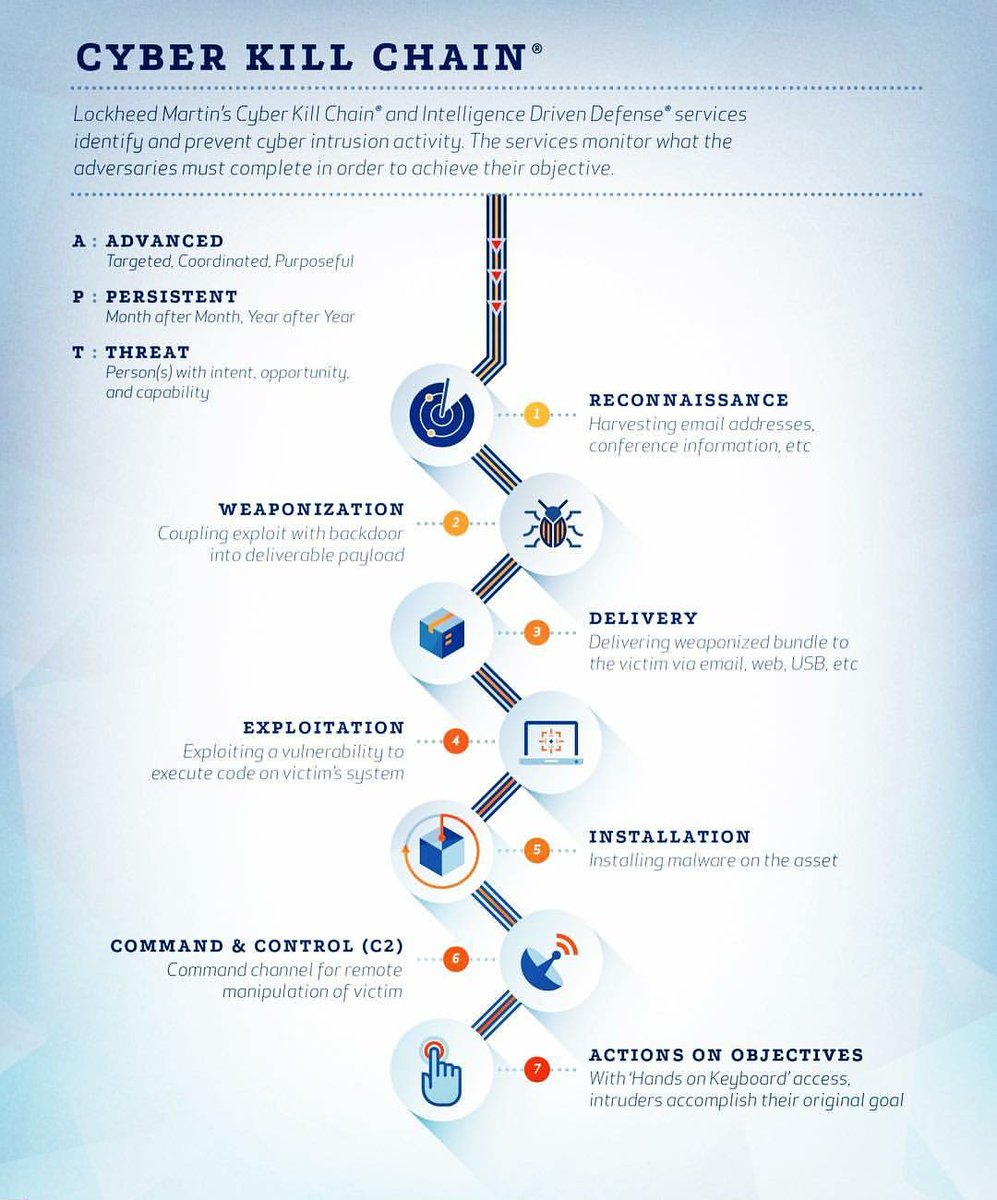
Shira Rubinoff The Cyber Kill Chain Cybersecurity Cybercrime Cyberattack Security Ransomware Malware Ddos Technology Ht Thecybersechub Via Lockheedmartin Cc Ipfconline1 Evankirstel Mikequindazzi Jimmarous
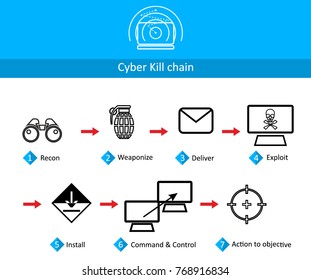
S 5llkvx32ljym
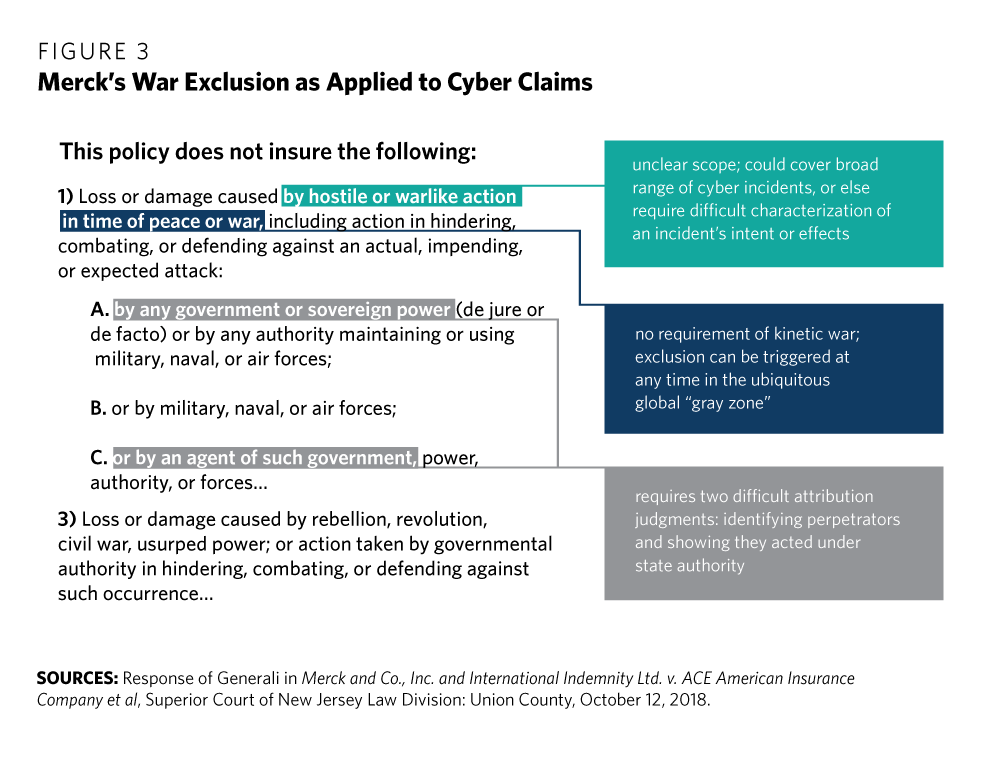
War Terrorism And Catastrophe In Cyber Insurance Understanding And Reforming Exclusions Carnegie Endowment For International Peace
Cyber Kill Chain Deutsch のギャラリー
Q Tbn And9gct5 B6sgmedusgpuntibrblyrtjmde7 3pen7soxcxoevyxlz6w Usqp Cau
Www Mitre Org Sites Default Files Publications Pr 18 1174 Ngci Cyber Threat Modeling Pdf

Sans Security Awareness Since 11 Numerous Versions Of The Cyber Kill Chain Have Been Released Read As Lspitzner Explains How The Human Element Addresses The Original Lockheed Martin Cyber Kill

Spark Your Splunk With Intsights
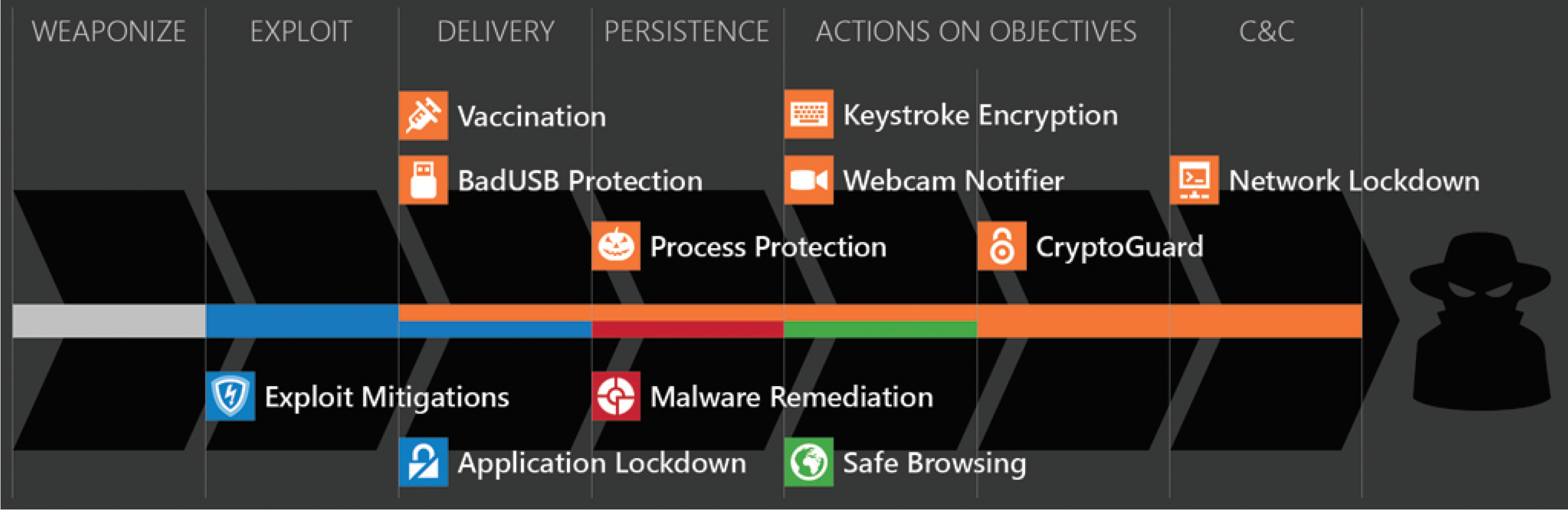
Hitmanpro Alert Gratis Download Cybertense
Magecart Delivered Via Advertising Supply Chain

Fireeye Adds Web Shell Detection To Protect Servers Fireeye Inc
Cyber Kill Chain
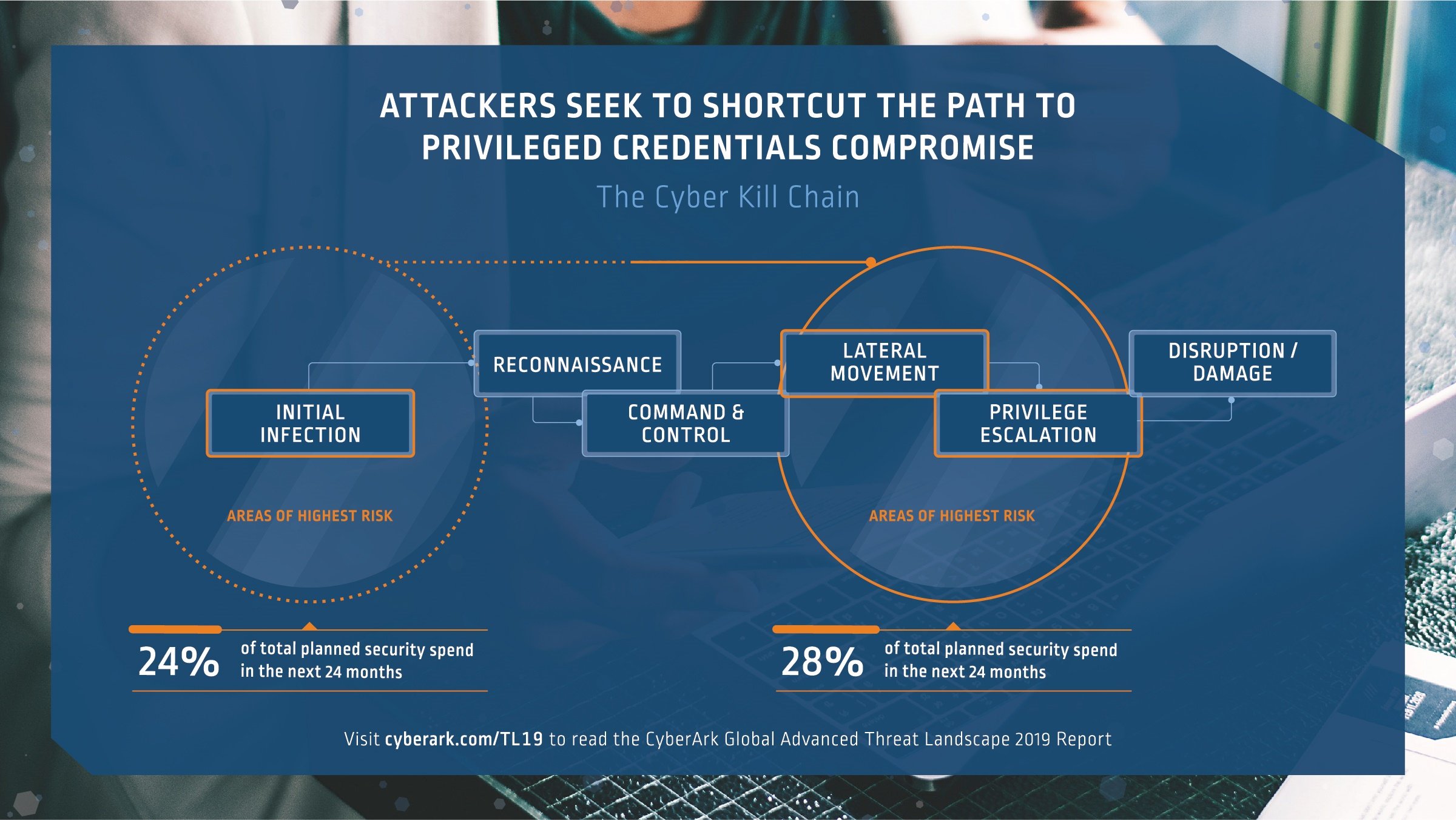
Are You Spending In The Right Places To Break The Cyber Kill Chain
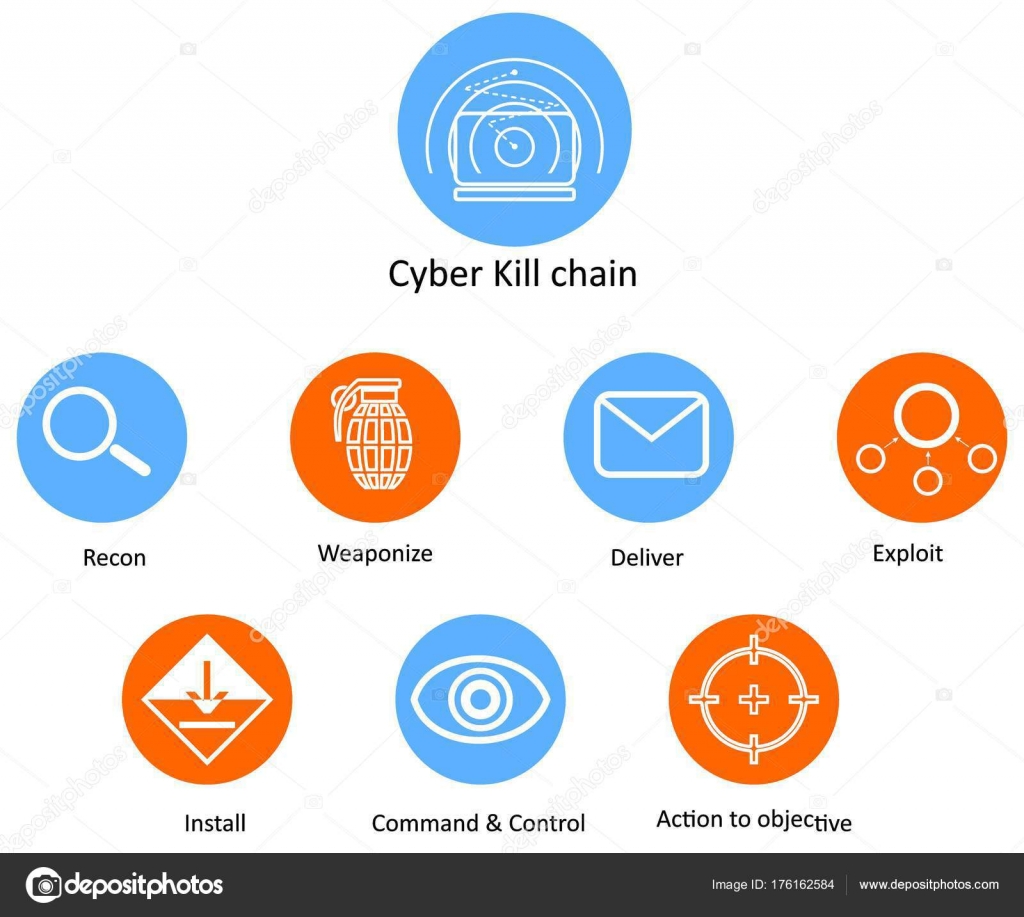
Cyber Kill Chain Stock Vector C Caribia
What Is A Cyber Attack Check Point Software
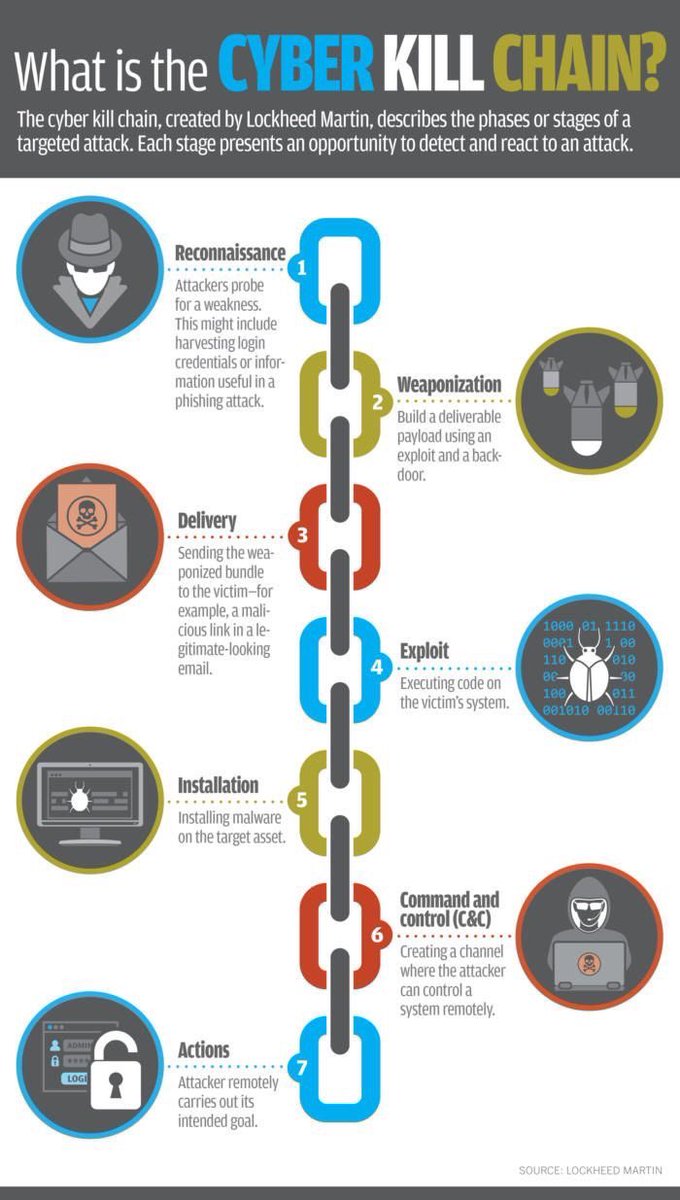
Wmpdigitalpcso What Is A Cyber Kill Chain Detect React Cyberkillchain Cyberattack Cybersecurity Infosec Cybercrime Weakness Exploit Code Phishing Malware Asset Remoteaccess Cyberprotect T Co 8u9lhu1xtq
Panda Cyber Kill Chain On Behance
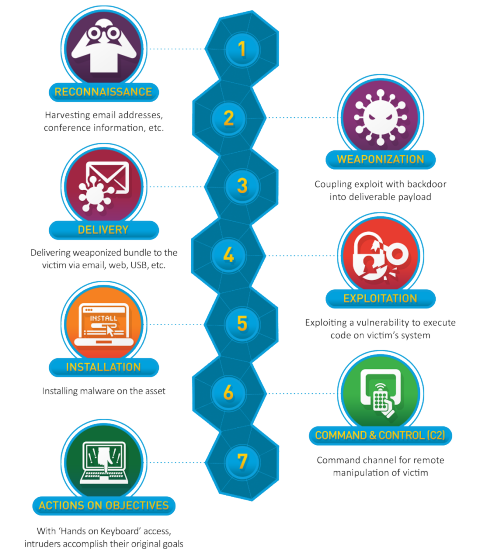
Cyber Kill Chain Lockheed Martin

Cyops1 1 Chp13 4 Computer Security Security

7 Key Best Practices For Cloud Security From Alert Logic Aws Partner Network Apn Blog
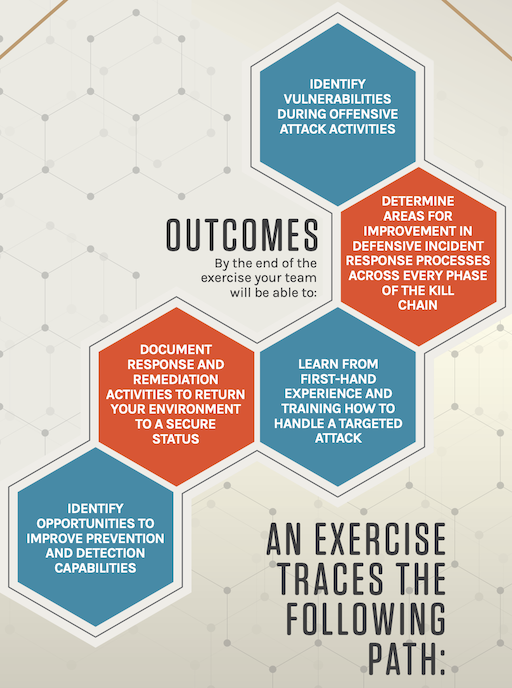
Red Team Vs Blue Team In Cybersecurity Crowdstrike

The Term Kill Chain Is Originally A Bizbrolly We Build Software For Mobile And Web Facebook
Www Csacademy Nl Images Scripties 18 Paul Pols The Unified Kill Chain Pdf

Cyber Kill Chain Stock Vector C Caribia

Protect Your Business From Cyber Attacks Crayon Us
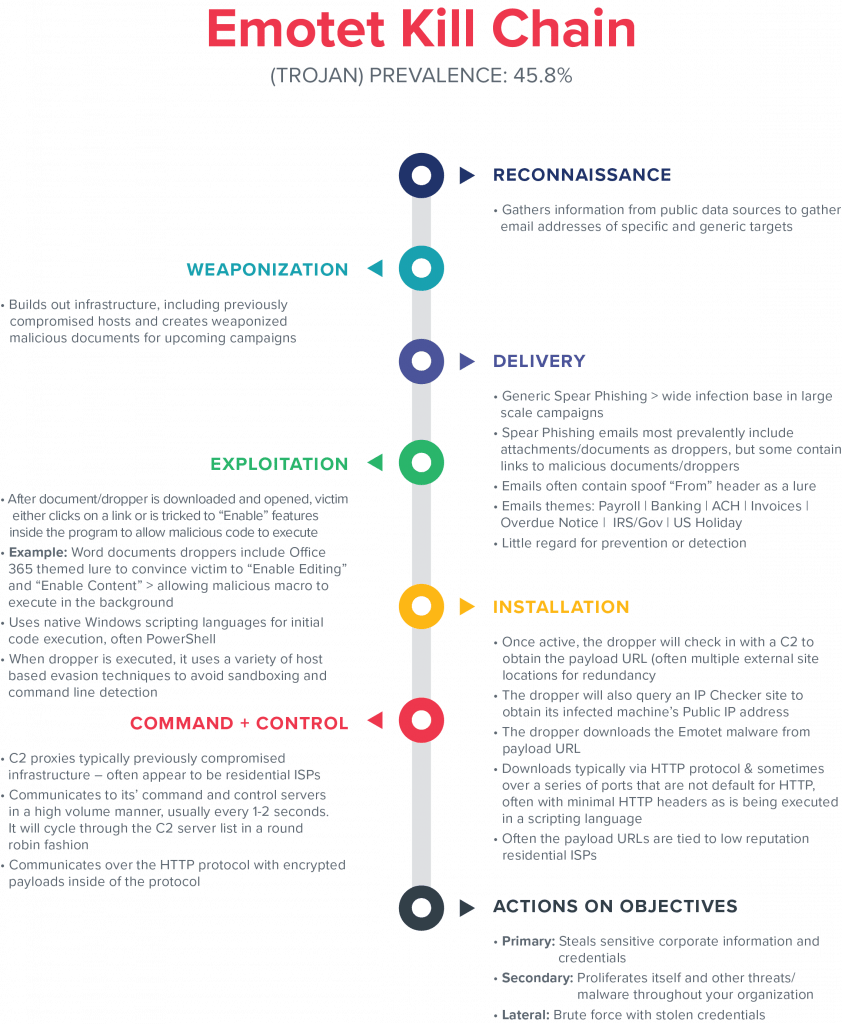
Three Families In Three Days Revisiting Prolific Crimeware To Improve Network Detection Emotet Gigamon Blog

Global Ransomware Attack Cisco
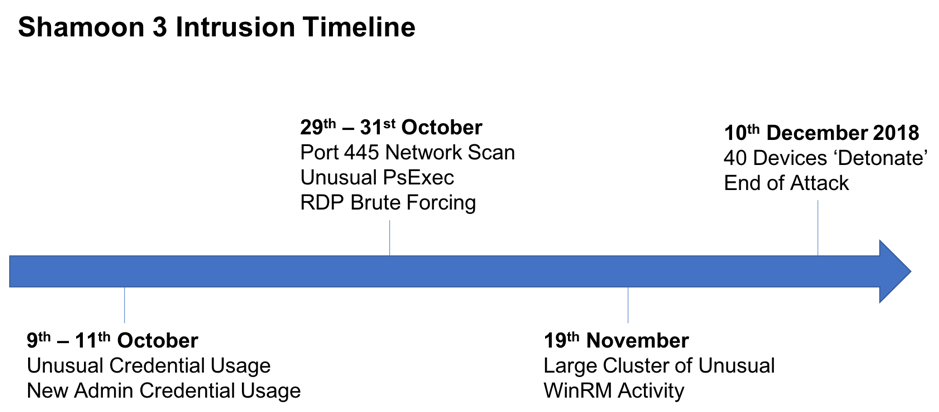
Shining A Light On Shamoon 3 What Cyber Ai Revealed About The Data Wiping Malware Blog Darktrace

Cyberattack Wikipedia

Fortinet Launches Global Threat Intelligence Service

Check Point

Tracking Your Adversary With A Threat Intelligence Platform

What Is Mitre Att Ck And How Is It Useful From Anomali
Q Tbn And9gcso2ajaym22auf2mt4fa 1m7yiwk8pa8dpl W6c9x Xlqzp78dm Usqp Cau
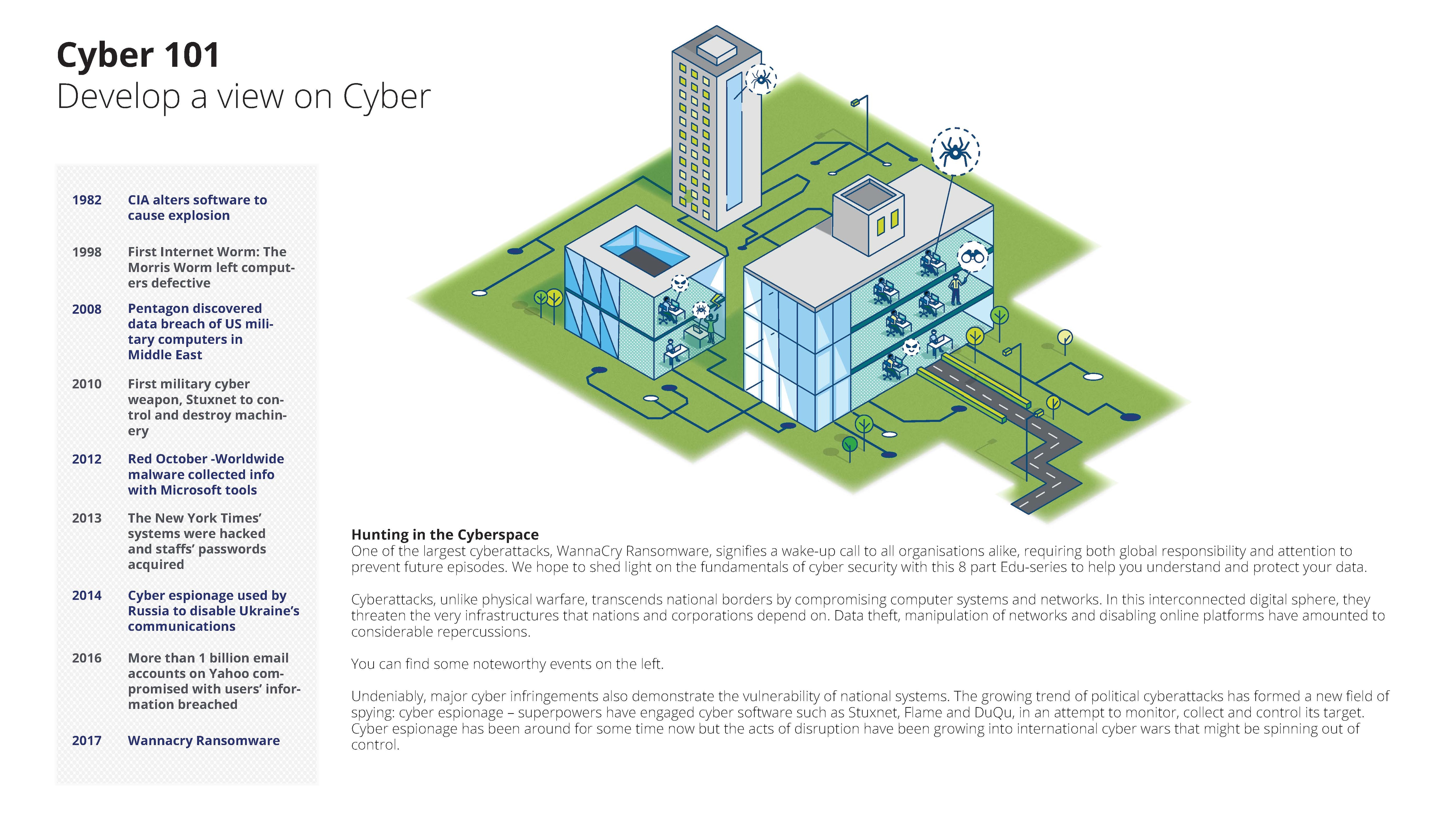
Anatomy Of A Cyber Attack Part 3 Deloitte Sea Risk Advisory

Darktrace Ot Threat Finds Defending The Widening Attack Surface Blog Darktrace

Kill Chain Inside The Bad Guy S Lair Micro Focus Blog

Enterprise Incident Response Getting Ahead Of The Wave Malwarebytes Labs Malwarebytes Labs

The Cyber Kill Chain Model Strenghten It Security Within Companies
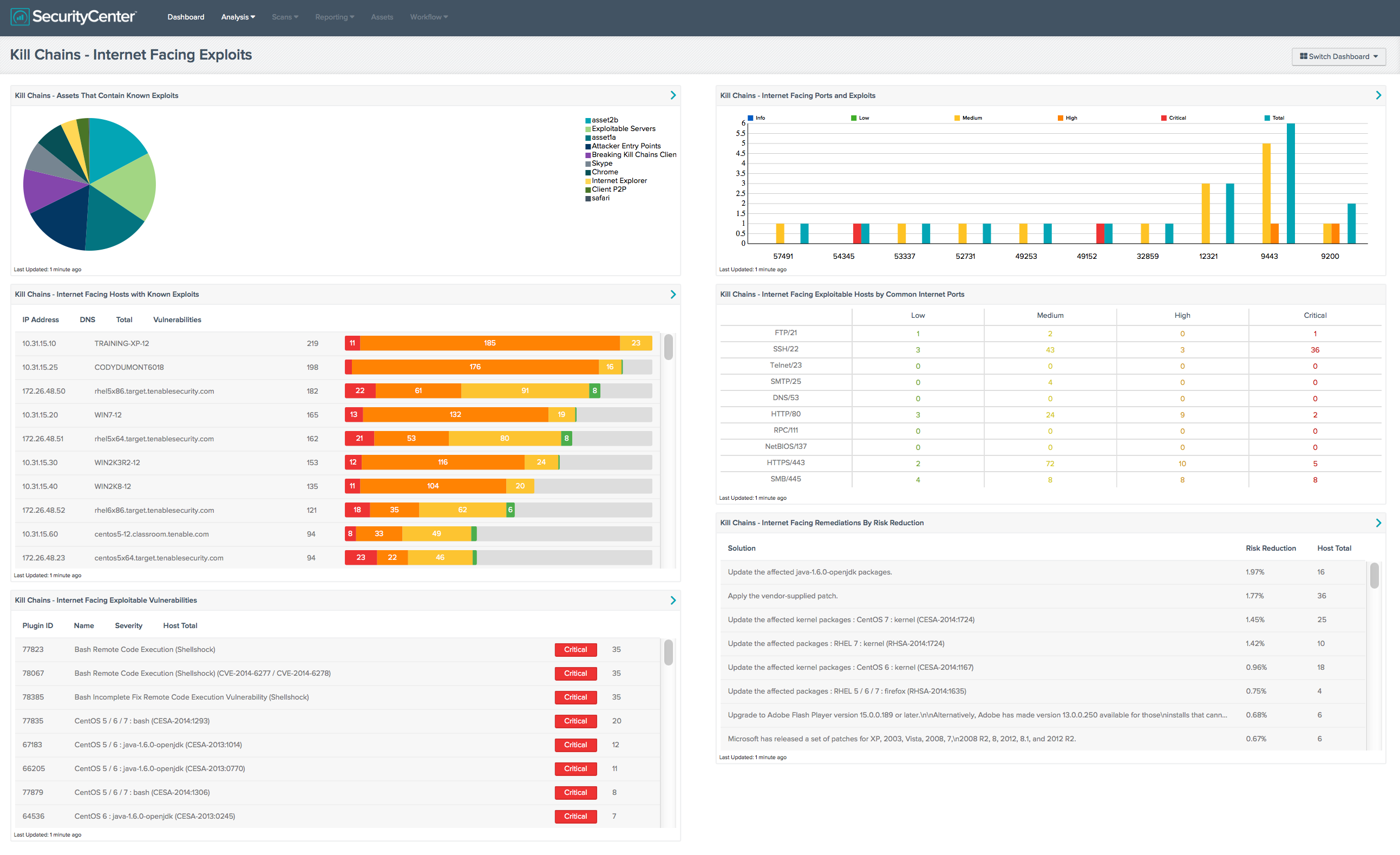
Identifying The Weakest Links In Cyber Kill Chains Tenable
Yasha Levine Lockheed Martin S Cyber Kill Chain Hackers Giving You Trouble Get Your Cyber Kill Chain On Today Only 10 E Z Payments Of 1 Billion Dollars T Co Bstyt47bae T Co Apvg3fsykv

Socradar Cyber Intelligence Inc Linkedin

Endpoint Detection And Response Threat Hunting And Incident Response For Hybrid Deployments Vmware Carbon Black

What Is Good Network Analysis F Secure Blog

Crowdstrike Falcon Endpoint Protection Platform Demo Crowdstrike

How Analytic Frameworks Lay The Groundwork For Applying Security Intelligence

Decoding Email Security Infradata Netherlands
Kill Chain Wikipedia
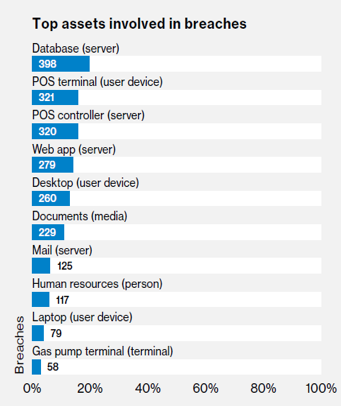
The Data Breach Kill Chain Early Detection Is Key Imperva
Wissen Ist Macht So Funktioniert Die Mitre Att Ck Matrix It Daily Net

Clearswift And Cyber Kill Chain Clearswift

What Is The Cyber Kill Chain And How To Use It Effectively Varonis

What Is Emotet Definition Infection Chain And Protection

Understanding Network Intrusions With The Cyber Kill Chain Whatsup Gold
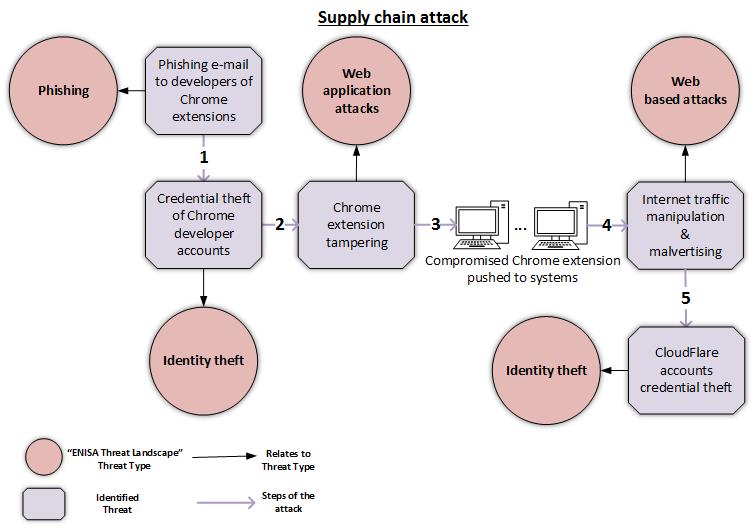
Supply Chain Attacks Enisa

Cyber Denial Deception And Counter Deception Springerprofessional De
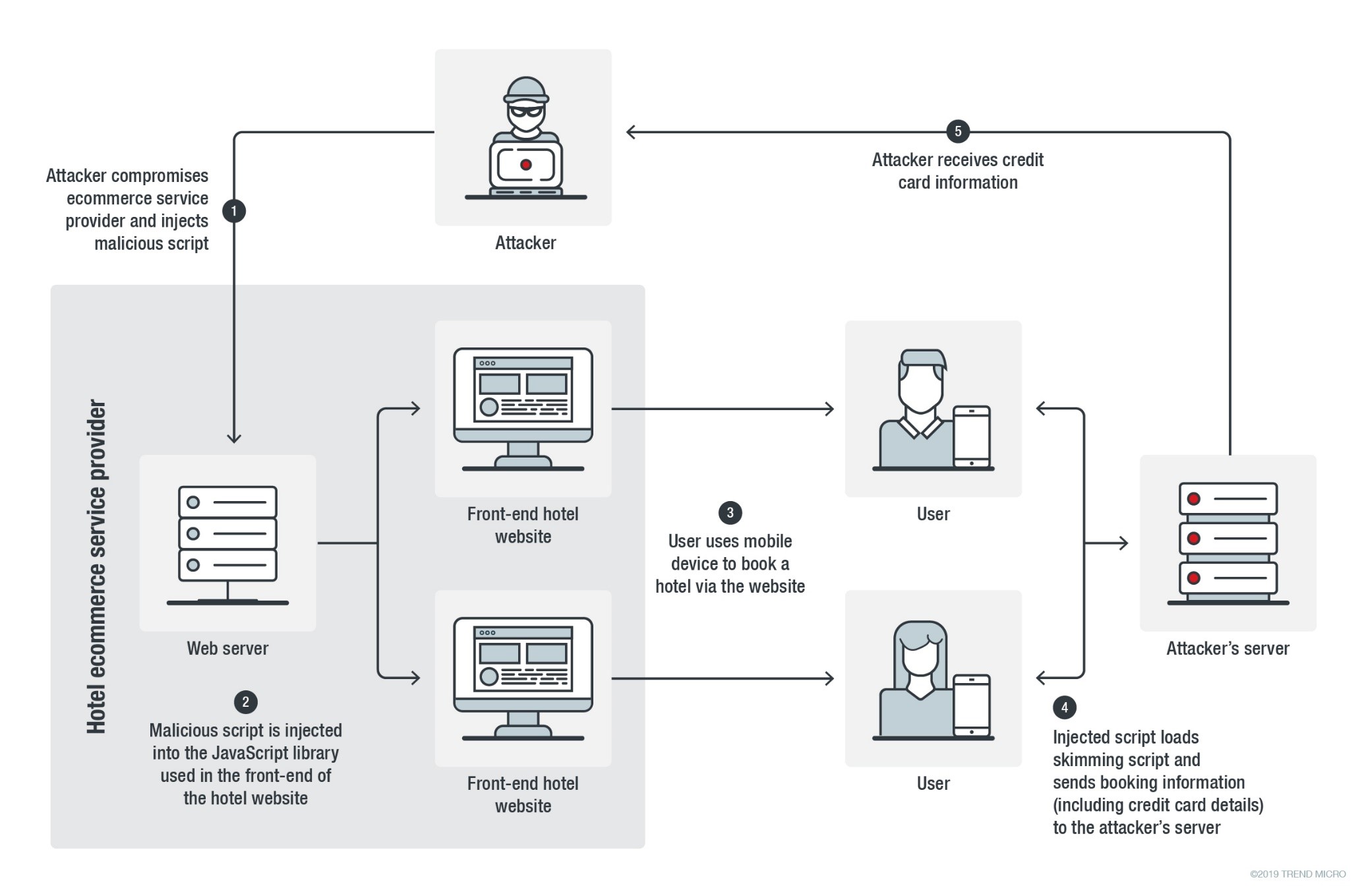
Magecart Targets Hotel Booking Websites On Mobile

Kill Chain Inside The Bad Guy S Lair Micro Focus Blog

The Cyber Kill Chain Mittelstand Techtag
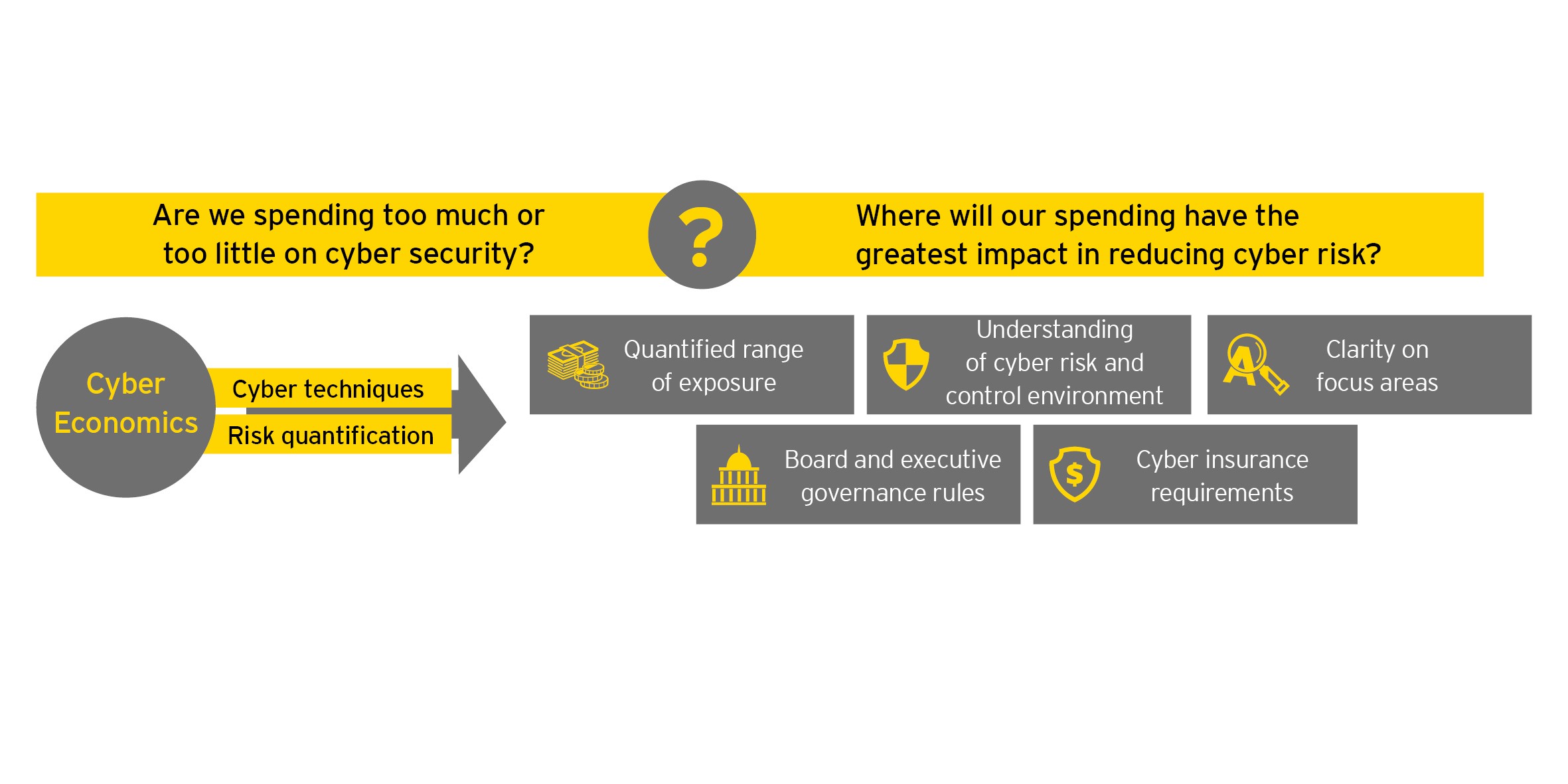
Assessing Cyber Risk Strategies The Right Way Ey New Zealand

Malicious Powershell Detection Via Machine Learning Fireeye Inc
:quality(80)/images.vogel.de/vogelonline/bdb/1228900/1228926/original.jpg)
Die Cyber Kill Chain In Der Cloud
.png)
Andromeda An Attack Kill Chain Analysis Forcepoint
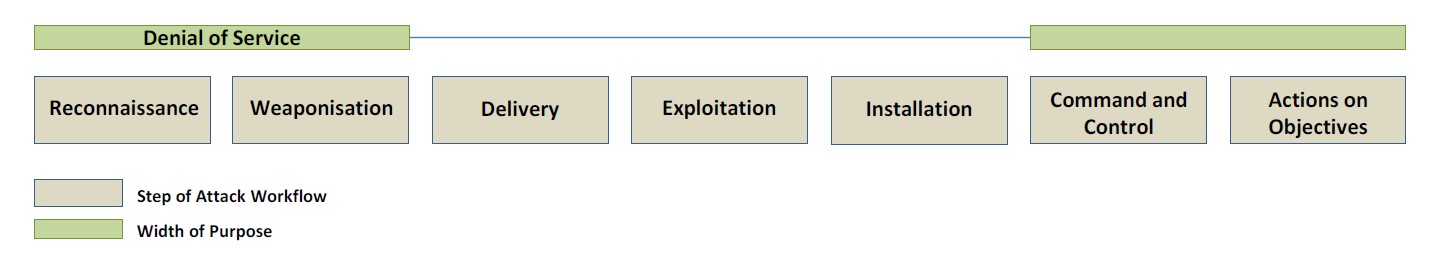
Ddos Kill Chain Enisa

Cyber Kill Chain Lockheed Martin
Www Hsdl Org View Did
Digitalcommons Usu Edu Cgi Viewcontent Cgi Filename 0 Article 4805 Context Smallsat Type Additional

Q5bg9tk4guy2bha0iwxw Pptx Cyberwarfare Security
Panda Cyber Kill Chain On Behance

Ransomware Protection And Advanced Threat Prevention
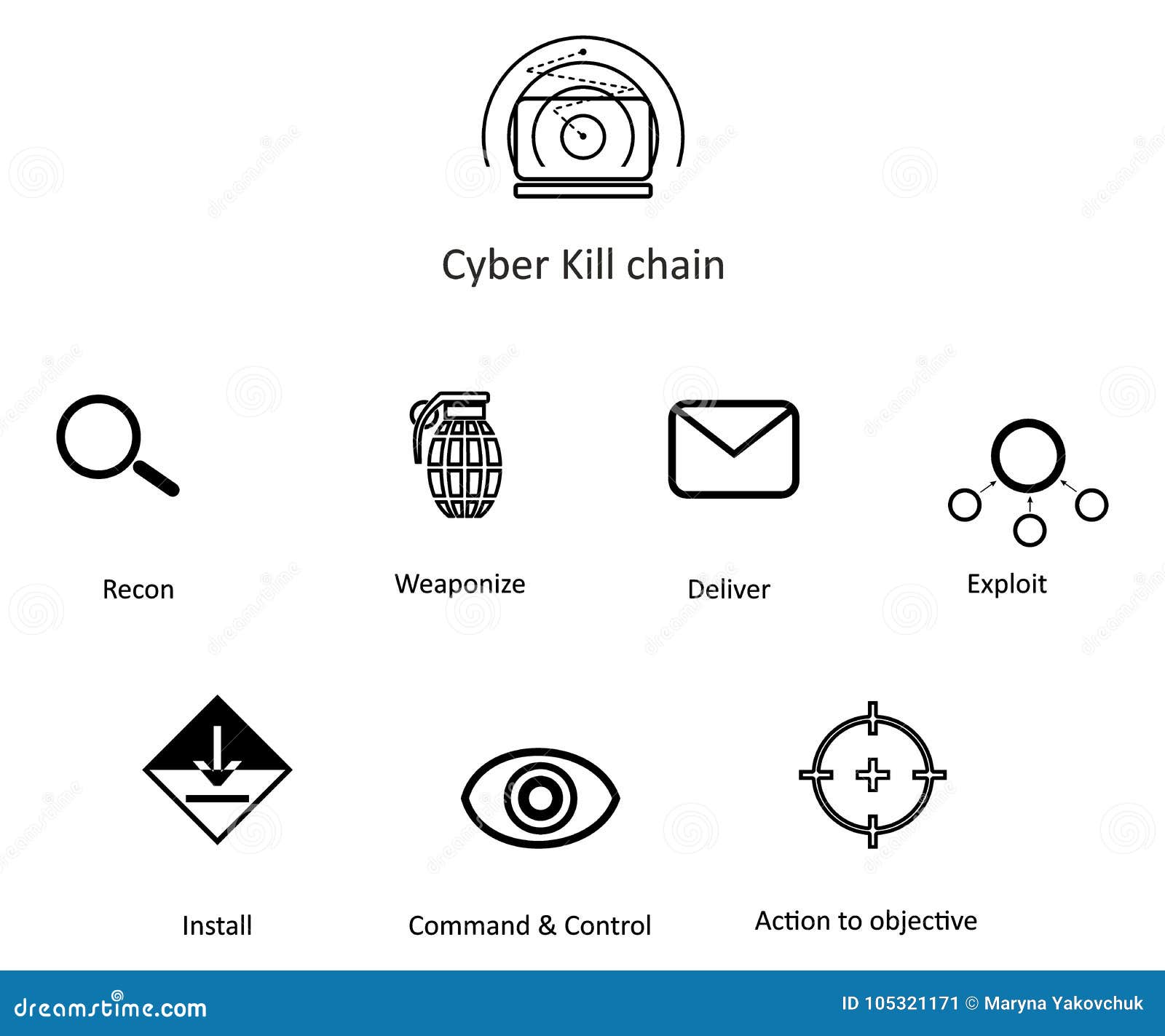
Cyber Kill Chain Stock Vector Illustration Of Corporate
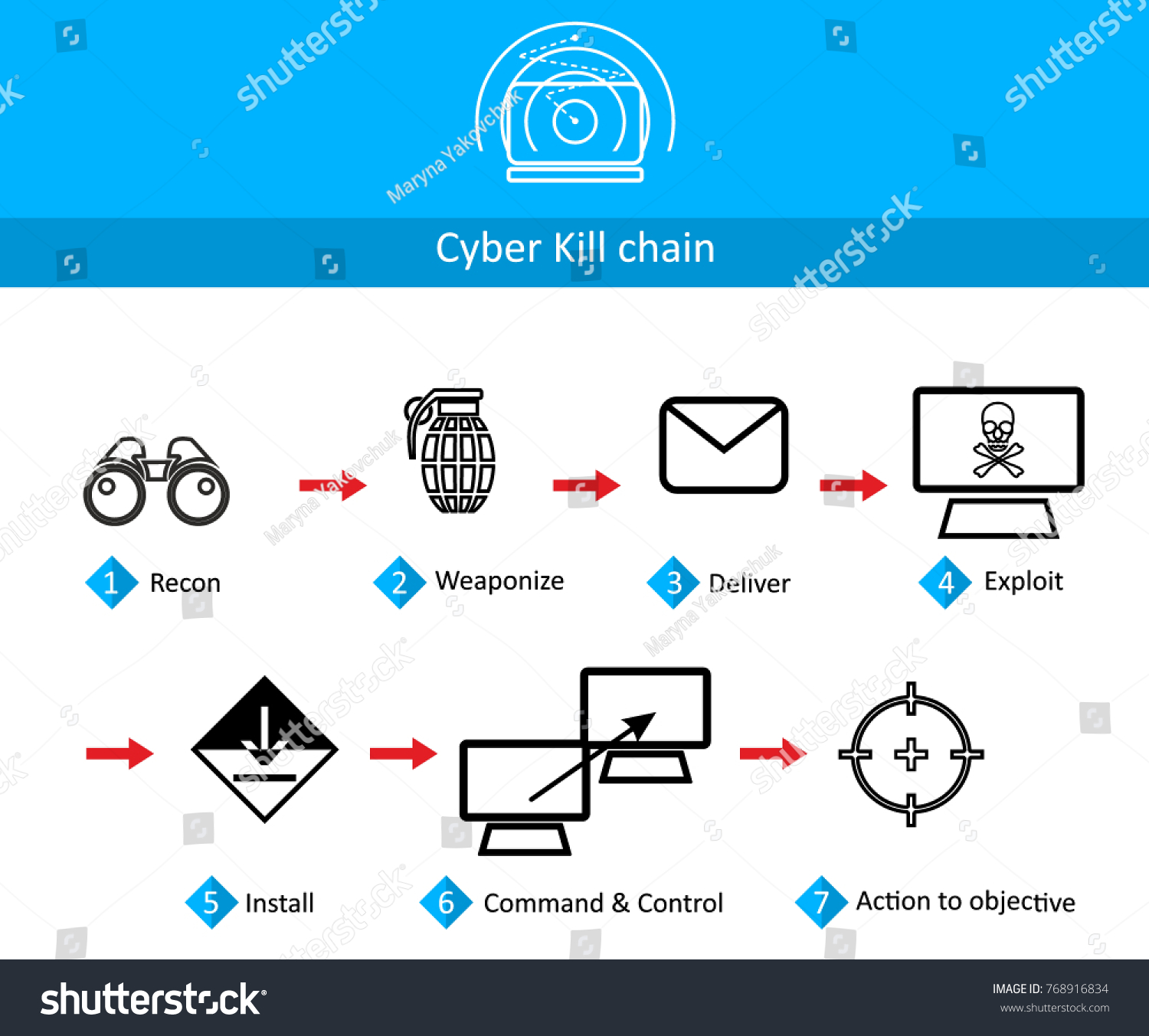
Illustration Style Flat Design On Theme Stock Vector Royalty Free

Pdf Estimating The Global Cost Of Cyber Risk Methodology And Examples

The Complete Guide To Understanding Mitre S Att Ck Evaluation Sentinelone

Cybercriminals Are Increasing Efficiency With Coordinated Attacks Enisa
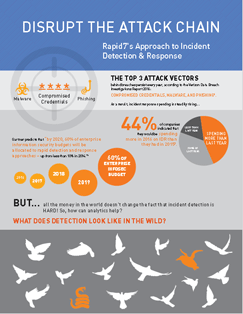
The Attack Chain Incident Detection Response

Decoding Email Security Infradata Netherlands
How Blackberry Protects You Against The Growing Menace Of Ransomware Attacks Everything You Need To Know About Stopping Today S Most Sophisticated Ransomware Attacks

The Data Breach Kill Chain Early Detection Is Key Imperva

Cyber Kill Chain It Infrastruktur Gezielt Schutzen

Legacy Security Solutions Come Up Short With Mobile Phishing

Advanced Threat Protection Cloud Delivered Zscaler
Www Osti Gov Servlets Purl

Elk Stack Security Analytics Elastic
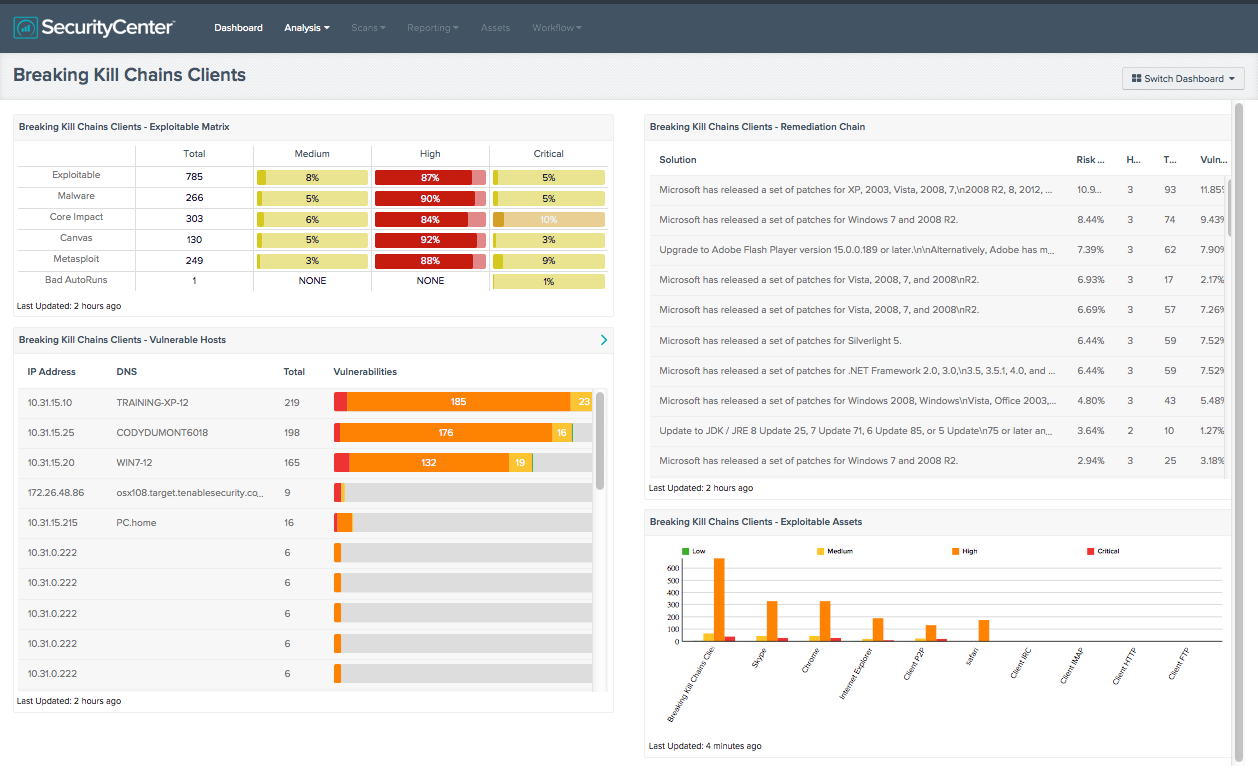
Identifying The Weakest Links In Cyber Kill Chains Tenable

Overview Of The Cyber Kill Chain Tm

What Is Mitre Att Ck And How Is It Useful From Anomali
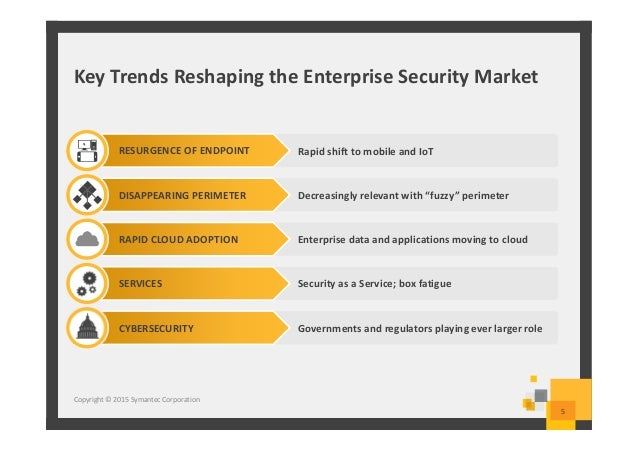
Addressing The Cyber Kill Chain
Www It Bildungsnetz De Fileadmin Media Akademietag 18 Pr Cisco Academy Security Pdf

How Can Threat Intelligence Help The Cyber Attack Kill Chain Recorded Future
Q Tbn And9gcrr9wgofqm Hyyd3 Pqxakclyqibi2ipnljyo4pqsvjm7 Rstau Usqp Cau
Www Cmu Edu Mits Files Breaking The Ddos Attack Chain Pdf
Addressing The Cyber Kill Chain
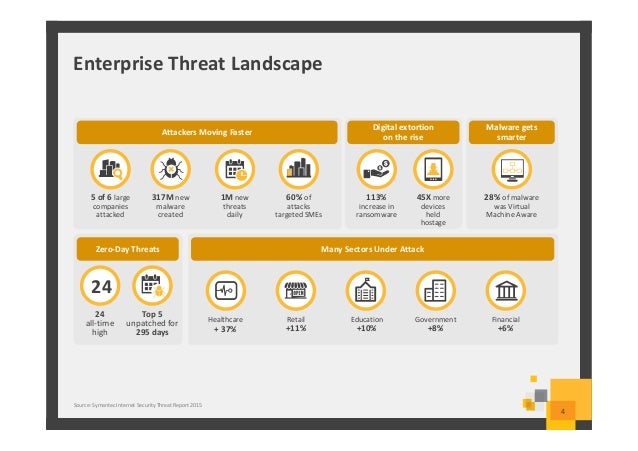
Video The Cyber Attack Lifecycle

Combating Cybercrime Deutsche Bank
1

Kill Chain Cyberattack Anfall Kill Purple Angle Png Pngegg
Www Ecs Org Eu Documents Uploads Understanding Cyber Ranges From Hype To Reality Pdf

5 Steps In The Mobile Phishing Kill Chain

What Is The Cyber Kill Chain And How To Use It Effectively Varonis

What Is The Cyber Kill Chain And How To Use It Effectively Varonis
Cyber Kill Chain Lockheed Martin
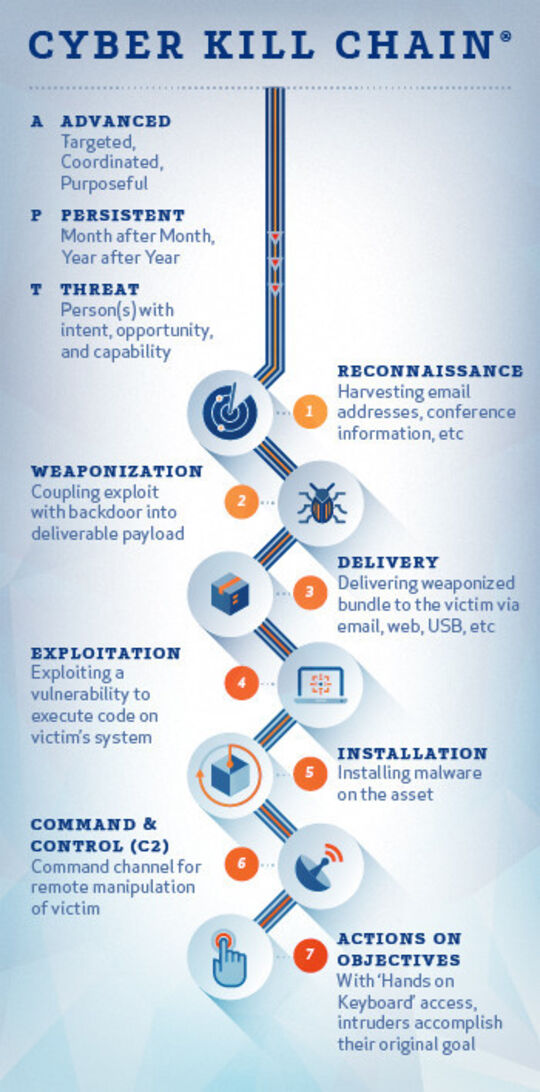
Cyber Kill Chain Als Basis Fur Mehrstufigen Schutz
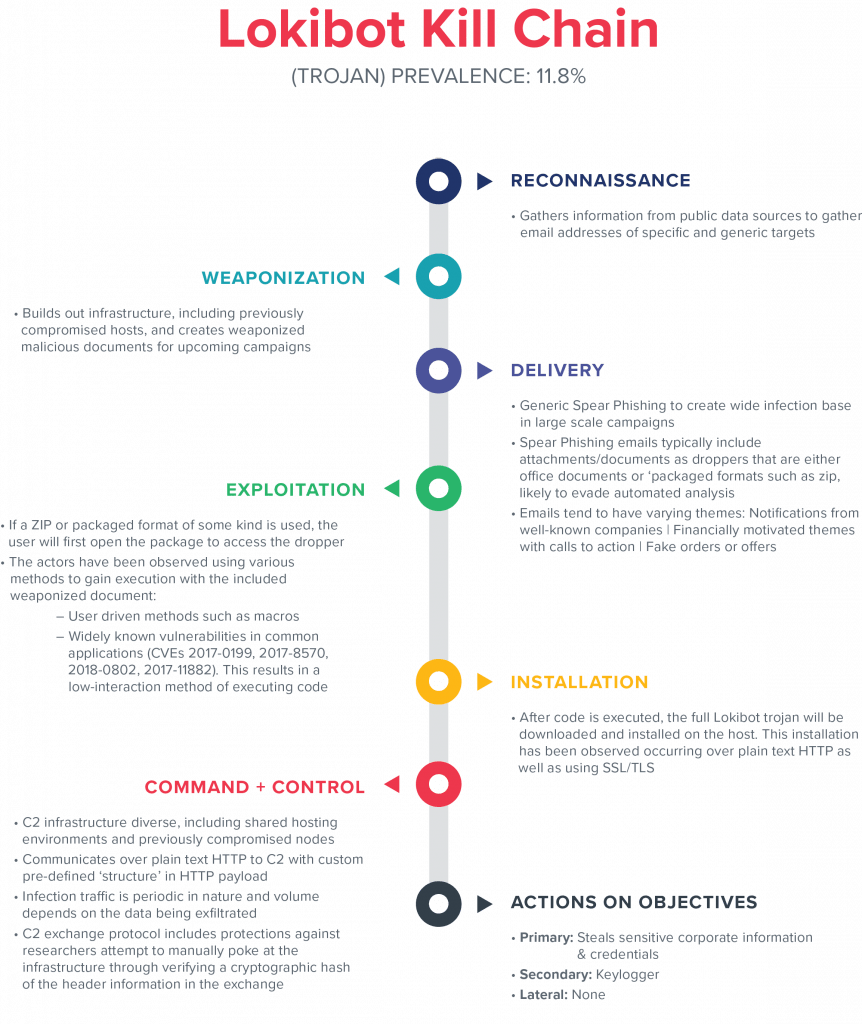
Three Families In Three Days Revisiting Prolific Crimeware To Improve Network Detection Lokibot Gigamon Blog

7 Key Best Practices For Cloud Security From Alert Logic Aws Partner Network Apn Blog



