Example Of Perimeter Protection
On the contrary, the recent Address Hotel fire in Dubai on December 31, 15 (New Year Eve) is a living example of an effective passive fire protection including the perimeterThe exterior burnt, but the perimeter fire barrier prevented flames, smoke and toxic gases from spreading inside the building.
Example of perimeter protection. KEY PRINCIPLES OF AN EFFECTIVE PERIMETER SECURITY PROGRAM Deter A fortified site is the optimal deterrent to attackersCommonly, perimeter fences / barriers, plus other visible mechanisms such as perimeter intrusion detection systems (PIDS), lighting and cameras serve as deterrents to a wouldbe attacker. Beyond a router, which connects the internal and external networks, the primary technology that underpins perimeter protection is a firewall, which filters out potentially dangerous or unknown traffic that may constitute a threat based on a set of rules about the types of traffic and permitted source/destination addresses on the network. Perimeter Protection is supported for the following IVS Features Tripwire, Intrusion, Fast Moving This guide will use Tripwire as an example, but the steps will be identical for the other Rule Types to add an Object Filter 8 Click 'Draw Rule' to draw the detection 9 Click inside the video frame to begin drawing the TripWire.
Endpoint Protection is Critical in Light of Expanding, Undefined Security Perimeter The rise of BYOD and the use of external storage devices have created an everchanging security perimeter for modern organizations that’s nearly impossible to define. Perimeter security intrusion detection system Illuminating the camera field of view with an Infrared (IR) or whitelighting system significantly improves the performance of the camera Ensuring optimum illumination for any perimeter application is crucial for achieving top level security and safety at night. Keep up to date with advances in perimeter security For example, Perimeter Intrusion Detection Systems (PIDS) have reached a level of reliability that means they are being used more and more Previously, the rate of false alarms meant these systems were often turned off, but now people have greater confidence in installing these systems.
Keep up to date with advances in perimeter security For example, Perimeter Intrusion Detection Systems (PIDS) have reached a level of reliability that means they are being used more and more Previously, the rate of false alarms meant these systems were often turned off, but now people have greater confidence in installing these systems. IP67 and IK09 rated, allweather approved. Understanding IT Perimeter Security 5 Define your perimeter Any network owner is required to know the full layout of the enterprise network But if every node is the perimeter itself, then the layout of the network is less of an issue with regard to the perimeter boundaries.
Definition of Perimeter explained with real life illustrated examples Also learn the facts to easily understand math glossary with fun math worksheet online at SplashLearn SplashLearn is an award winning math learning program used by more than 30 Million kids for fun math practice. This system gives intruders electric shocks, so it is not allowed in all countries, for example in Europe it can only be done in critical installations and with specific permits Microphone cable fence disturbance sensors It is a perimeter protection system by cable that runs along the entire fence. Perimeter Protection 4 PIDAS OA mutually supporting combination of barriers, clear zones, lighting, and electronic intrusion detection, assessment and access control systems constituting the perimeter of a Protected Area and designed to detect, impede, control or deny access to the Protected Area (PA).
The perimeter protection security should protect residents and other people located within the protected area from any sort of intrusion, including spying activities To meet this goal, the perimeter protection system should use multiple layers of protection, which include not only mechanical and physical protection, but also advanced. IP67 and IK09 rated, allweather approved. Take a highrise building, for example There, perimeter security consists of a lock on the door," says Wood "Then, there are other facilities that have a large perimeter that includes double fencing with motion sensors inbetween the fences, closedcircuit television, security patrols, guard stations, limited access, etc" The Plan.
Outdoor perimeter security is an oftenoverlooked area of physical security design that can dramatically improve the effectiveness of a facility’s security system If you are involved in designing or managing physical security the infrastructure located in the buildings likely consumes the majority of your budget However, small investments in outdoor perimeters can provide significant. Perimeter protection products are designed to create a barrier and capture stormwater Silt fences and straw wattles are prime examples of perimeter protection products, but we offer additional solutions based on your needs. Perimeter protection products are designed to create a barrier and capture stormwater Silt fences and straw wattles are prime examples of perimeter protection products, but we offer additional solutions based on your needs.
Some types of perimeter access controls are fences and walls;. Targets), target perimeter, security perimeter, perimeter security, attacks and threats, and risk are addressed The second section of the report builds from the first and presents several models which, taken together, provide a general conceptual framework for considering the need for, and nature of, standards for perimeter security. The (D)evolution of the Perimeter In the beginning, maintaining a highlevel of protection from cyber threats was very much focused on securing the perimeter This was the golden age of firewalls, VPNs and DMZs (Figure 1) Trust was, essentially, established and defined by the perimeter At this point in time, the lifeblood of the company.
Perimeter security barriers steel, cast iron, reinforced concrete, and granite (or other stone) The advantages For example, routine painting is necessary to prevent rust Reinforced concrete barriers take more time and manpower to install, but require little maintenance and are typically less expensive than steel or cast iron. The perimeter of a building is the area around a structure or property Sometimes the term perimeter security is used to describe all the security that prevents entry into a building itself Most commonly, perimeter security means boundaries besides the exterior of a structure, such as walls and other fortifications 1 Locks. Typical perimeter security begins with a fence and gate and may include multiple security methods (eg, card access, locks, sensors, lighting, CCTV, and patrols) to increase protection (Fig 92) Technology can extend security surveillance beyond the perimeter, as illustrated with radar that is applied at a facility near a waterway ( Fig 93 ).
Vehicle barriers Work out if your organisation needs perimeter access controls during your security risk assessment and before you complete any site selection process Fences and walls Fences and walls are used to define and secure the perimeter of a facility. Beyond a router, which connects the internal and external networks, the primary technology that underpins perimeter protection is a firewall, which filters out potentially dangerous or unknown traffic that may constitute a threat based on a set of rules about the types of traffic and permitted source/destination addresses on the network. Perimeter Protection The value of perimeter protection is emphasized as far more than just motion detection when you consider the environmental factors around the area in question For example, at Chicago’s Navy Pier, standard motion detection will not achieve perimeter protection over Lake Michigan, because the movement of the waves themselves would hide the real target, thus making the application useless.
Perimeter Protection 4 PIDAS OA mutually supporting combination of barriers, clear zones, lighting, and electronic intrusion detection, assessment and access control systems constituting the perimeter of a Protected Area and designed to detect, impede, control or deny access to the Protected Area (PA). Local Perimeter It is common for an organization's internal network to have multiple zones that are each protected by a network perimeter For example, a bank may isolate backend servers such that only specifically authorized IPs may establish a network connection. Understanding IT Perimeter Security 5 Define your perimeter Any network owner is required to know the full layout of the enterprise network But if every node is the perimeter itself, then the layout of the network is less of an issue with regard to the perimeter boundaries.
This system gives intruders electric shocks, so it is not allowed in all countries, for example in Europe it can only be done in critical installations and with specific permits Microphone cable fence disturbance sensors It is a perimeter protection system by cable that runs along the entire fence. Security Radar When monitoring large, exposed spaces with harsh weather, and where the perimeter environment is too complex for deployment of only video surveillance cameras, security radar is the ideal option Fewer false alarms using digital beamforming technology and intelligent analysis algorithms;. While many of the means to provide perimeter and interior security overlap (for example, security guards and cameras can protect your perimeter or interior), thinking in terms of these three levels, and trying to implement two or three physical security measures at each level, will help you to implement appropriate physical security measures.
Perimeter security has changed over time The perimeter is not the only thing to consider in a layered defense structure, but it is the first protection of the external world into organizational structures Over the last few years, with constant need for mobility, the positioning of the perimeter has changed substantially. The challenges of designing a multiunit residential, commercial or institutional access system become much more complex when client requirements include higher levels of perimeter security The need for a higher level of security comes into play when a breach creates potential for impact on revenue, data protection or the wellbeing of tenants. Perimeter protection via sensors starts at the barrier encircling the premises, such as a fence or wall, and ends at the building envelope In order to keep these areas secure, software inside the sensor evaluates all monitoring fields If someone or something intrudes into a monitoring field, an alarm is triggered Data measured by the sensors is used to determine the position of a person on.
Perimeter security barriers steel, cast iron, reinforced concrete, and granite (or other stone) The advantages For example, routine painting is necessary to prevent rust Reinforced concrete barriers take more time and manpower to install, but require little maintenance and are typically less expensive than steel or cast iron. Security and protection system, any of various means or devices designed to guard persons and property against a broad range of hazards, including crime, fire, accidents, espionage, sabotage, subversion, and attack Most security and protection systems emphasize certain hazards more than others In a retail store, for example, the principal security concerns are shoplifting and employee. Perimeter Protection is supported for the following IVS Features Tripwire, Intrusion, Fast Moving This guide will use Tripwire as an example, but the steps will be identical for the other Rule Types to add an Object Filter 8 Click 'Draw Rule' to draw the detection 9 Click inside the video frame to begin drawing the TripWire.
An example of outer layer perimeter security is monitoring the airspace with drone detection solutions to prevent corporate espionage and other attacks The inner layers are often ignored but are critical to mitigating insider threats Data Center Infrastructure Management. Perimeter protection via sensors starts at the barrier encircling the premises, such as a fence or wall, and ends at the building envelope In order to keep these areas secure, software inside the sensor evaluates all monitoring fields If someone or something intrudes into a monitoring field, an alarm is triggered Data measured by the sensors is used to determine the position of a person on. On the contrary, the recent Address Hotel fire in Dubai on December 31, 15 (New Year Eve) is a living example of an effective passive fire protection including the perimeter The exterior burnt, but the perimeter fire barrier prevented flames, smoke and toxic gases from spreading inside the building.
After you think you are safely proficient with the mind set of perimeter security devices, you can graduate yourself and augment to the trip wire reloadable retort devices like the 12 ga shotgun shell blaster These are on the internet for about $40 They can take a shotgun shell right out of the box but these don’t work well because it is. Perimeter control BMPs are the last protection before sediment enters the roadway, storm drains or adjacent properties Perimeter control BMPs can be the most visible and most vandalized BMPs used on a site of ground disturbance Perimeter BMPs shall be installed before starting and site grading activities Stormwater Control BMPs are. L WHITE PAPER l Perimeter Protection and Control SECURITY 3 This year we have seen a stepchange in the way in which we use and rely upon the connected world We have become more adept at using communication and collaboration tools in our personal and business lives, and the online economy for retail and services of all kinds has become.
A perimeter network is sometimes called a demilitarized zone or DMZ For perimeter networks to be effective, incoming packets must flow through security appliances hosted in secure subnets before reaching backend servers Examples include the firewall, intrusion detection systems, and intrusion prevention systems. Perimeter security is a key element for the protection of critical assets, and providers are looking for innovative solutions that can address their security concerns, especially for sites which. A very good reference for more ideas and information on physical perimeter security recommendations is the “Site and Urban Design of Security Guidance against Potential Terrorist Attacks, FEMA 430” It’s a free 272page comprehensive risk management document loaded with security examples and illustrations 6 Defend.
Security Radar When monitoring large, exposed spaces with harsh weather, and where the perimeter environment is too complex for deployment of only video surveillance cameras, security radar is the ideal option Fewer false alarms using digital beamforming technology and intelligent analysis algorithms;. Perimeter security is the philosophy of setting up functional apparatus or techniques at the perimeter of the network to secure data and resources It is part of the greater security field and has its own role in active system protection. Perimeter protection products are designed to create a barrier and capture stormwater Silt fences and straw wattles are prime examples of perimeter protection products, but we offer additional solutions based on your needs7.
One example of perimeter protection still in use is razor wire fencing While US ranchers in the 19th century kept the cattle in and the rustlers out with barbed wire, World War I saw the advent of specialized barbed wire to secure military operations. Perimeter protection products are designed to create a barrier and capture stormwater Silt fences and straw wattles are prime examples of perimeter protection products, but we offer additional solutions based on your needs. Example If a potential intruder comes to a perimeter security barrier or wall system that is lined every few feet with security lights, he can probably safely assume this is a wellsecured facility and that there is a good chance the intruder would be seen by security before/after attempting to breach the facility So the attempt ends before it starts.
The Chilean photovoltaic plant that required perimeter protection around extensive areas of land with few resources is one example of this Another example is the Louvre Museum in Abu Dhabi, which protects its 24,000metre facilities with a DAVANTIS security system made up of more than 400 surveillance cameras.
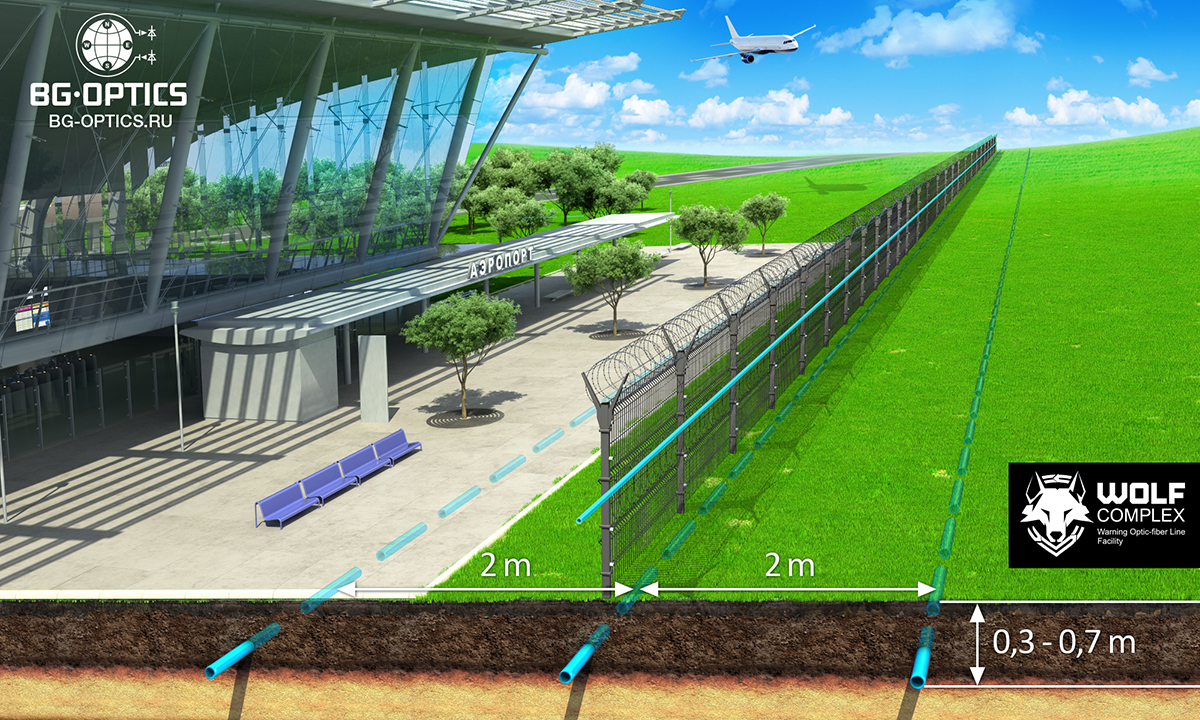
Bg Optics Is A Russian Manufacturer Of Critical Site Perimeter Security Systems Based On Fiber Optics
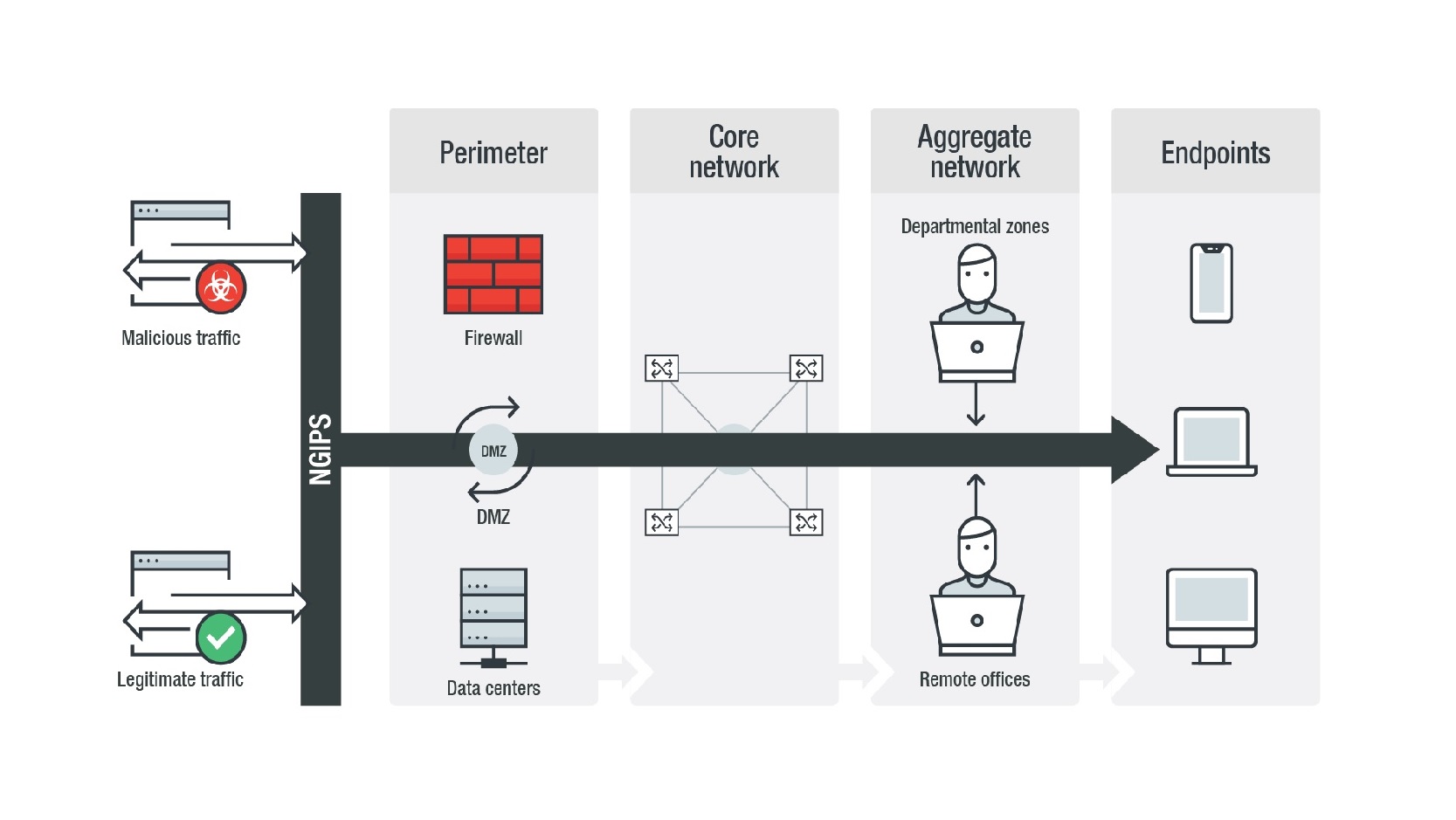
Guide To Network Threats Strengthening Network Perimeter Defenses With Next Generation Intrusion Prevention Security News

Perimeter Security Strategies For Data Center Protection Data Center Knowledge
Example Of Perimeter Protection のギャラリー
Dahuawiki

Perimeter Security What To Consider In A Camera Network Webcams Blog

Prison Perimeter Security For Correctional Facilities

Rrs Security Solutions Perimeter Intrusion Monitoring System

Cutting Edge Technologies For Port Surveillance And Monitoring Fax Tel Ppt Download

Perimeter Of Square How To Calculate Perimeter Of A Square

Perimeter Protection Solutions By Application Hikvision

Google Cloud Networking In Depth Three Defense In Depth Principles For Securing Your Environment Google Cloud Blog

Logical Security Network Perimeter Security It Security Plan

Perimeter Intrusion Detection System Pids Bandweaver Fo Sensing

Perimeter Security What To Consider In A Camera Network Webcams Blog

5 Best Practices For Complete Perimeter Security Flir Systems Security News Securityinformed Com
Zero Trust Security Complete Guide And How To Implement It

Perimeter Protection Solutions By Application Hikvision
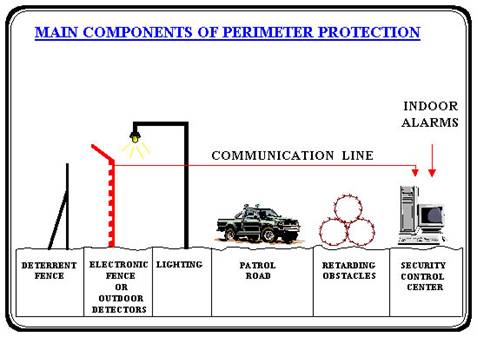
Perimeter Protection The Full Story A Z The Outer Defence Perimeter Protection

Perimeter Security An Overview Sciencedirect Topics

How To Think About Zero Trust Architectures On Aws Aws Public Sector Blog

Dahuawiki
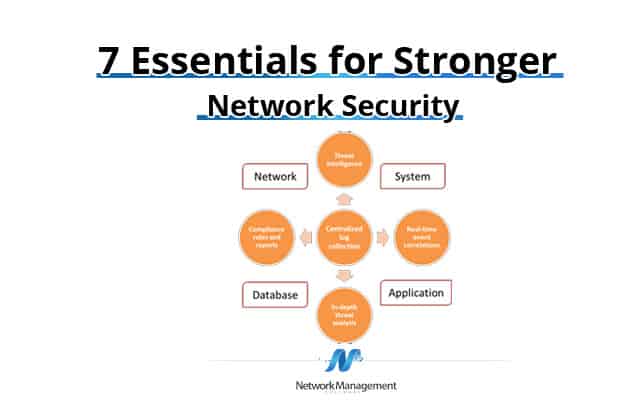
Network Security 7 Essentials For Stronger Netsec Protection 21
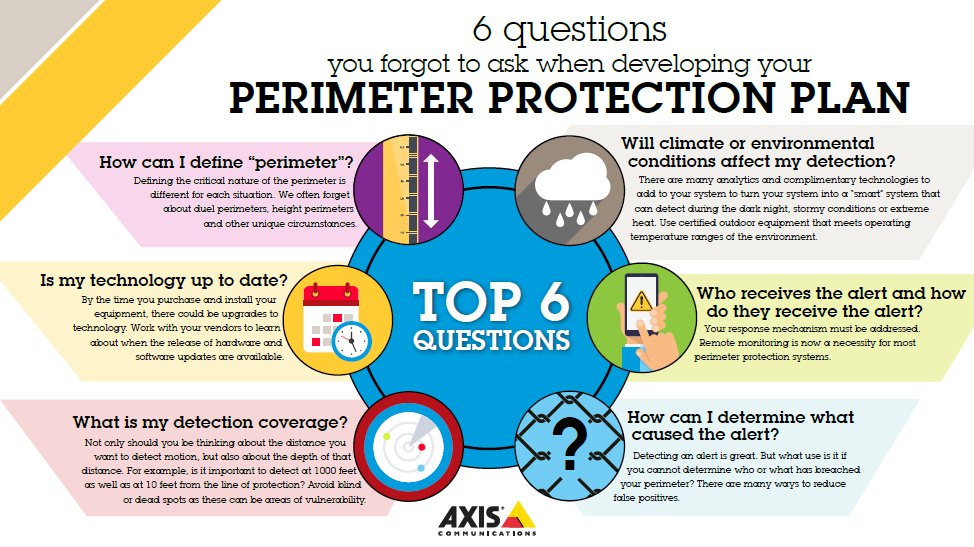
Axis Communications 6 Questions You May Have Forgotten To Ask When Developing Your Perimeter Protection Plan Blog Post T Co Hq6v9p9apy T Co Sjt6yuhzkt

Physical Security Managing The Intruder Infosec Resources
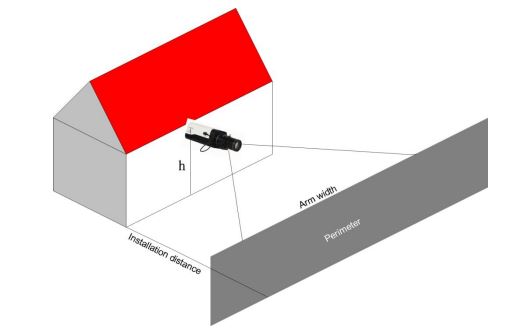
Dahuawiki

Perimeter Barrier Gate Bollard Sign Lan Security Today

Physical Security Wikipedia

Perimeter Security An Overview Sciencedirect Topics

Evitech Video Surveillance Intelligente Business Application
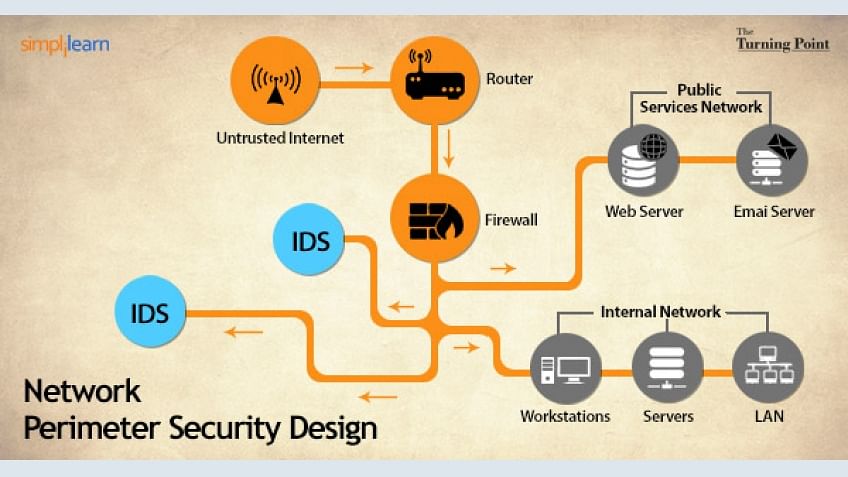
It Security Management Network Perimeter Security Design

Perimeter Protection System At Best Price In Udaipur Rajasthan Prompt Automation

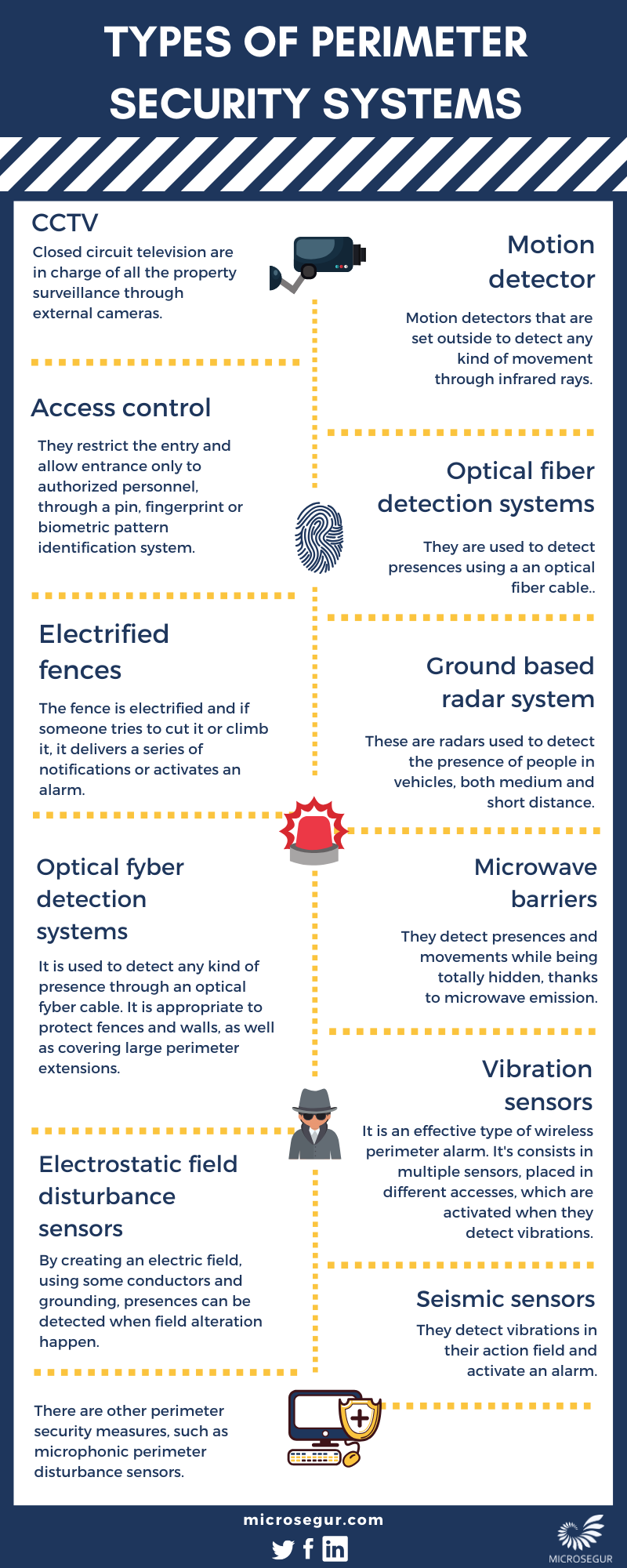
Types Of Perimeter Security Systems Microsegur

Perimeter Networks Cloud Adoption Framework Microsoft Docs

Perimeter Security Overview The Basics Panel Built

Layered Perimeter Protection For Apps Running On Aws Ctd1 R1 Aw

Perimeter Fence Wikipedia
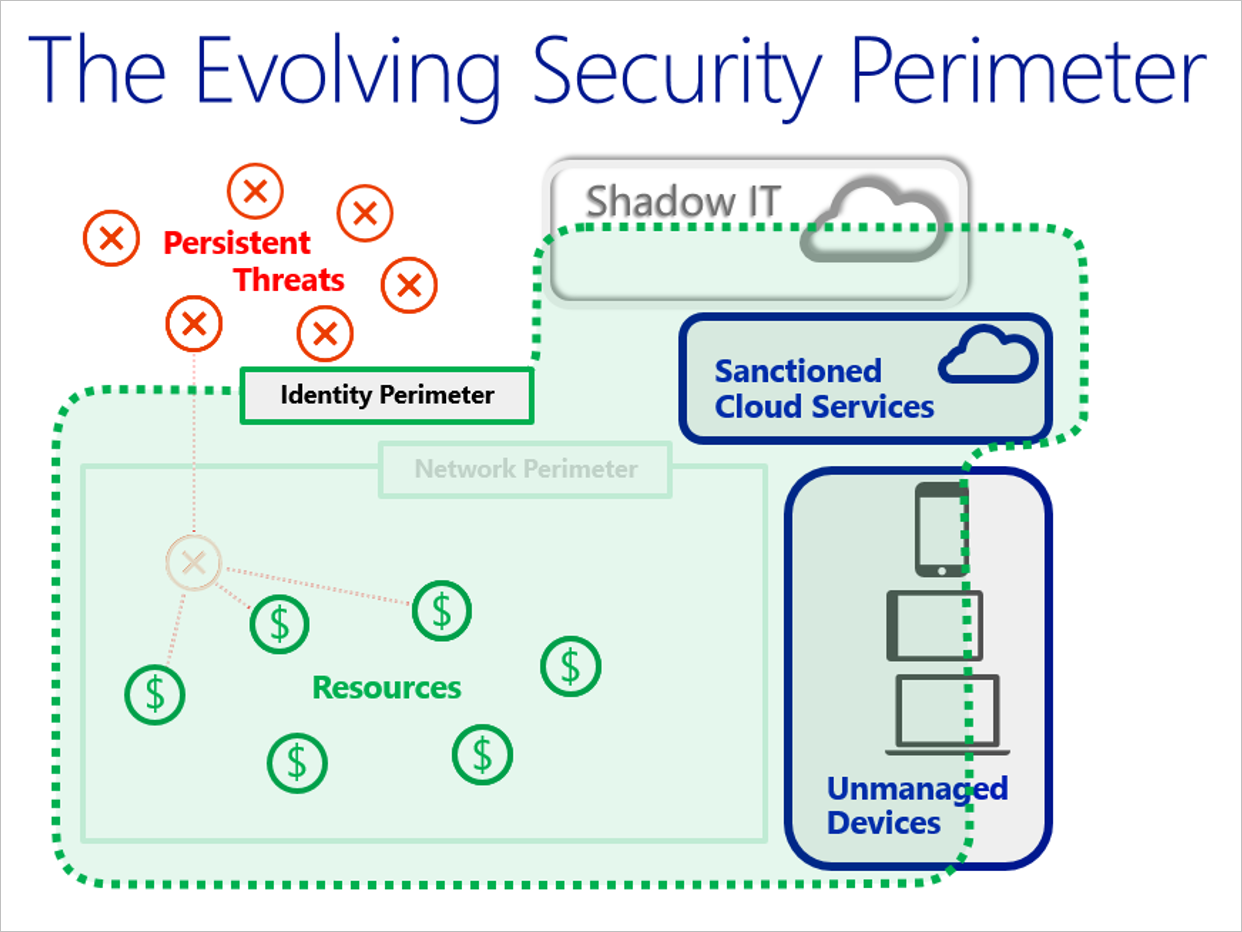
Best Practices For Secure Paas Deployments Microsoft Azure Microsoft Docs

Perimeter Barrier Gate Bollard Sign Lan Security Today

6 Perimeter Protection Best Practices Security Sales Integration

Perimeter Security Overview The Basics Panel Built
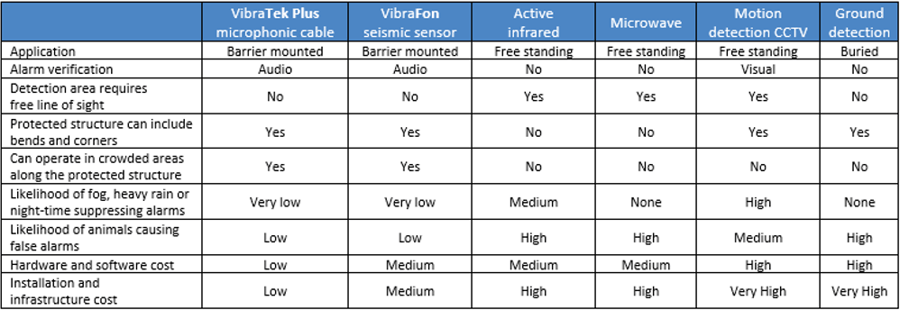
Pids Systems The Definitive Guide To Perimeter Intrusion Detection

Dynamic Perimeter Security With Ip Intelligence F5

How To Select The Right Perimeter Sensor To Fit Your Needs

The 5 D S Of Outdoor Perimeter Security 12 03 05 Security Magazine
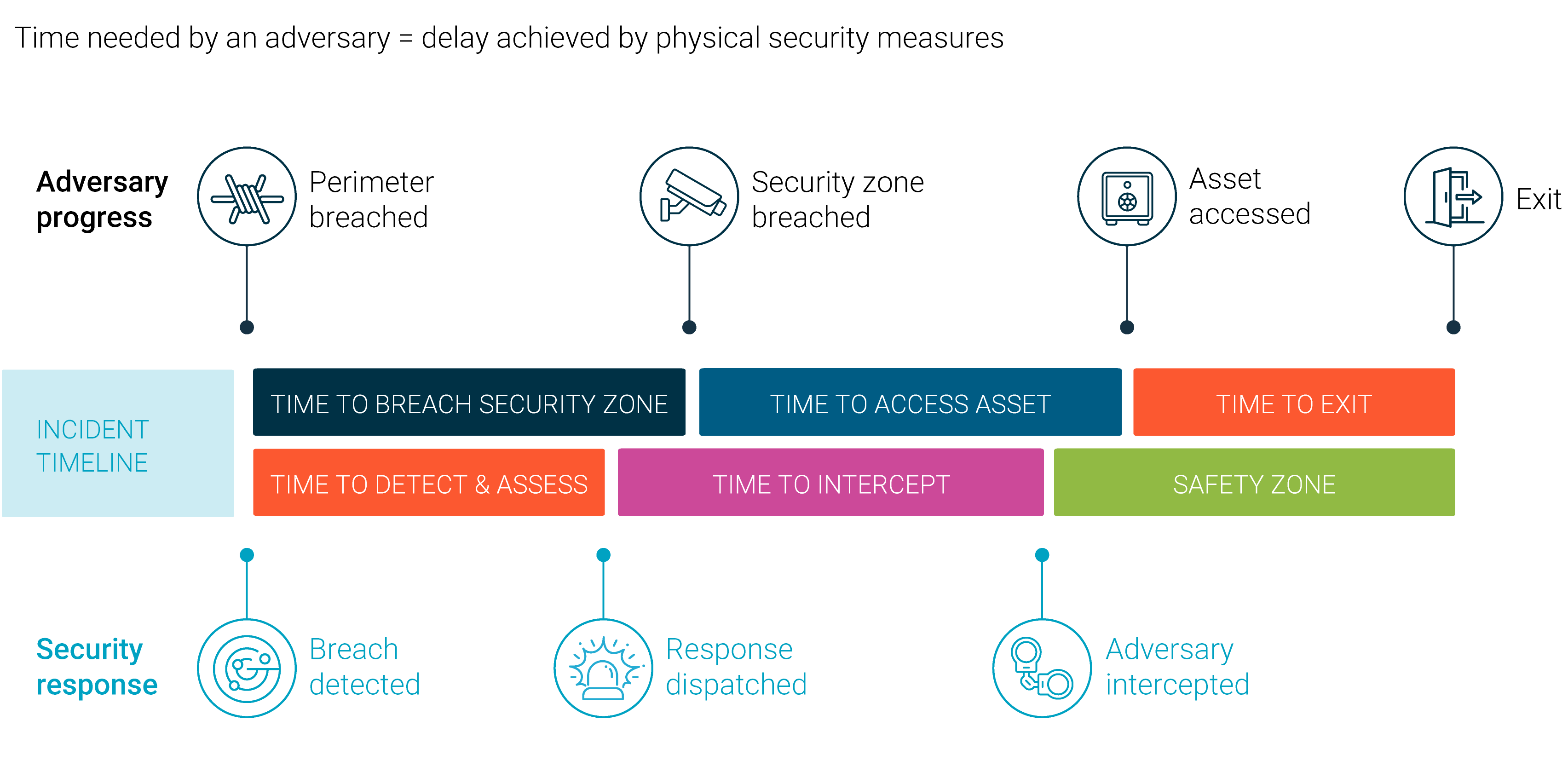
Security In Depth Protective Security Requirements

Dmz Tutorial Hosting Public Facing Servers Firewall Advanced Features

Protective Security Measures For Deter Detect And Delay At The Perimeter Public Website
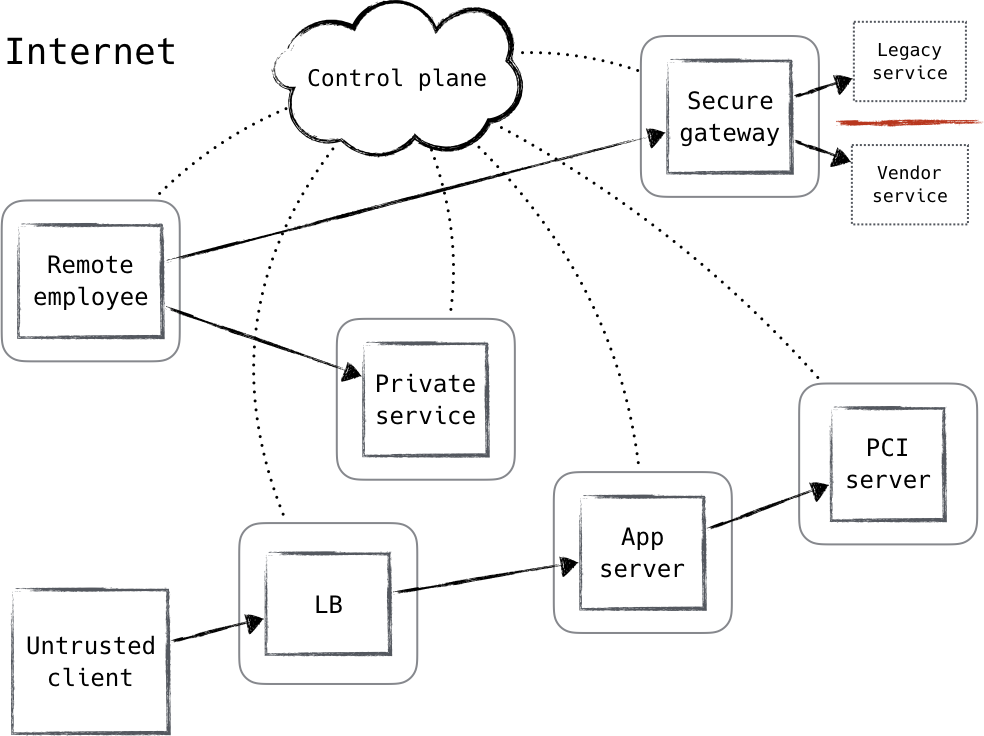
1 Zero Trust Fundamentals Zero Trust Networks Book
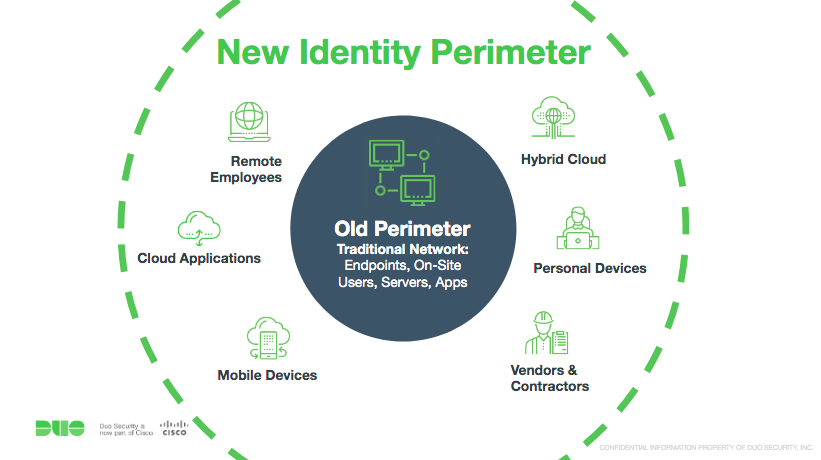
Zero Trust Evaluation Guide Securing The Modern Workforce Duo Security

The Need For Access Control Perimeter Protection Ppt Video Online Download

How To Think About Zero Trust Architectures On Aws Aws Public Sector Blog
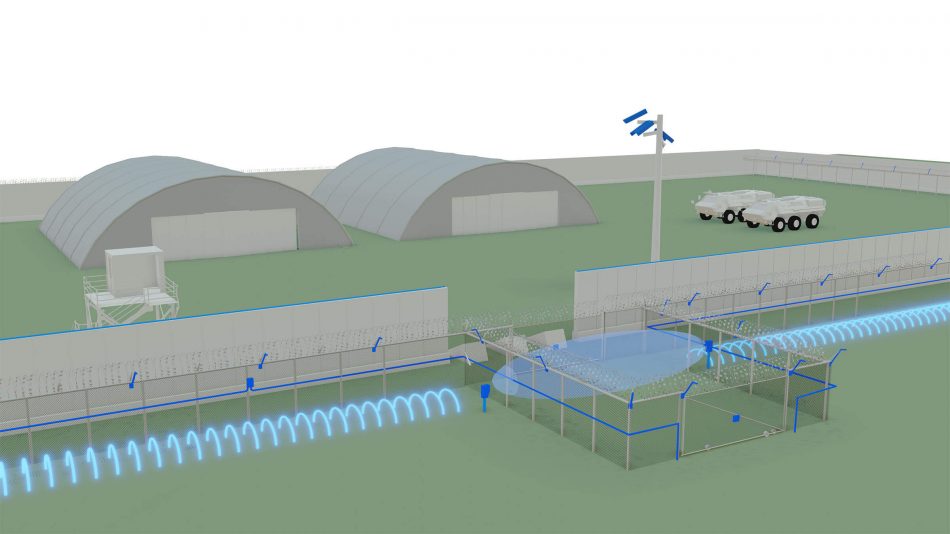
Senstar Border Protection And Security For Military Facilities Senstar
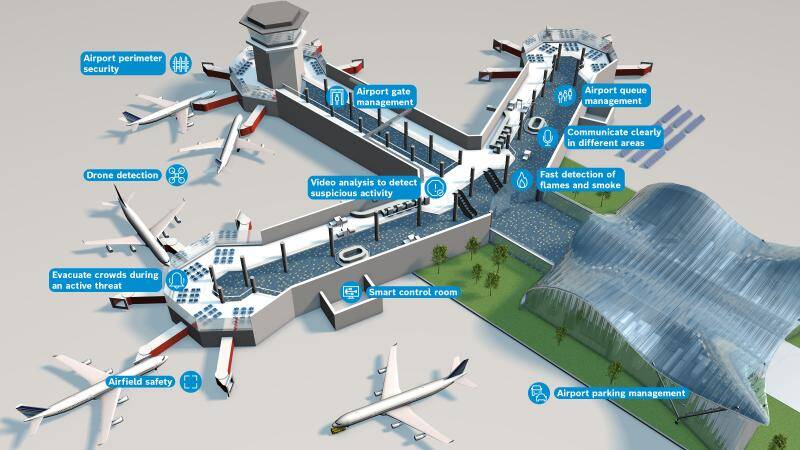
Airport Security Solutions Bosch Security And Safety Systems I Global

Pdf Information Perimeter Security Of The Organization Tjprc Publication Academia Edu

Types Of Perimeter Security Systems Microsegur

Fm3 90 Chapter 8 Basics Of Defensive Operations

Perimeter Protection Solutions By Application Hikvision

Building Zero Trust Networks With Microsoft 365 Microsoft Security

Perimeter Intrusion Detection The First Line Of Defense Security Info Watch

6 Perimeter Protection Best Practices Security Sales Integration

Why Traditional Network Perimeter Security No Longer Protects Help Net Security

Ppt Secure Globe Your Turnkey Partner In Airport Perimeter Security Projects Powerpoint Presentation Id

Multi Layer Perimeter Protection Solutions Aug 06 18 Singapore Malaysia Johor Bahru Jb China Vietnam Supplier Suppliers Supply Supplies Marc Corporation Pte Ltd

Perimeter Protection An Overview Sciencedirect Topics

Axis Communications Perimeter Protection Solutions Anixter

Security Resources Articles Whitepapers Stanley Security

The State Of The Physical Security Market 19 To 24

6 Perimeter Protection Best Practices Security Sales Integration
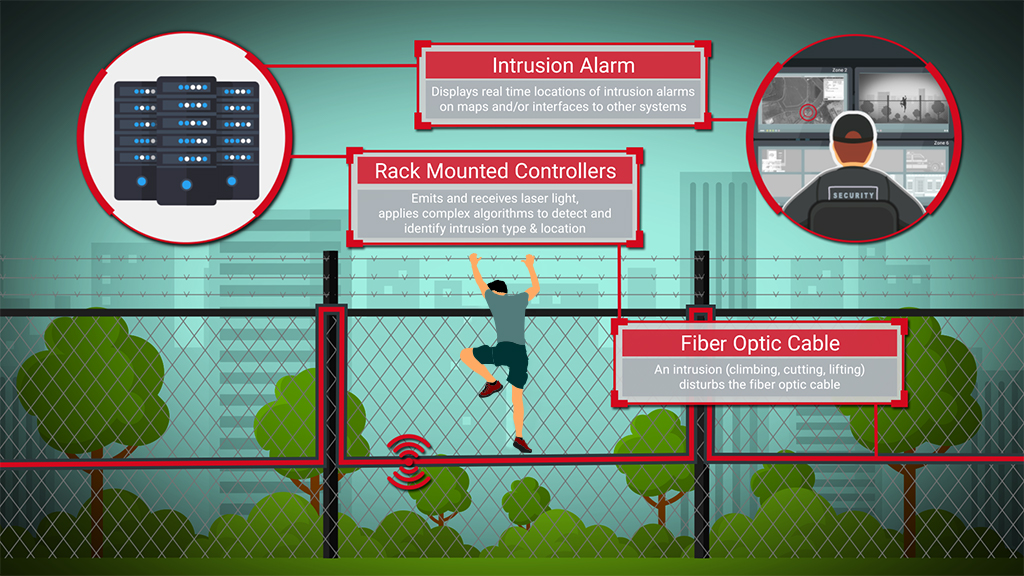
Perimeter Intrusion Fft

Perimeter Security Michael Ofstedahl

Physical Security Wikipedia
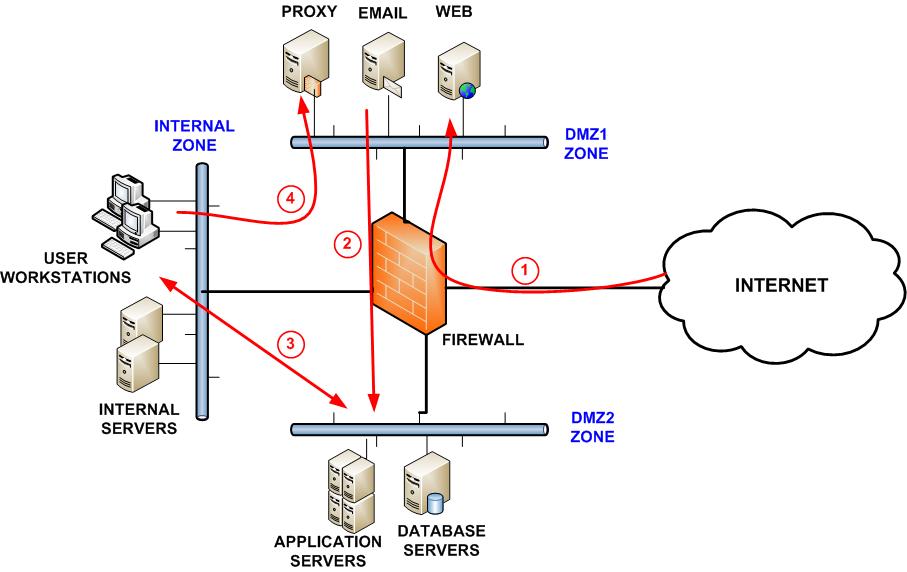
Best Firewall Security Zone Segmentation For Optimal Network Security
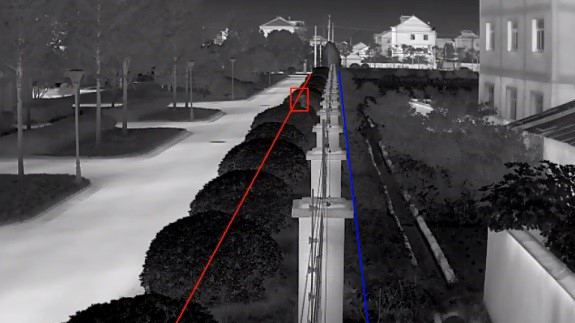
Perimeter Protection Solutions By Application Hikvision

Physical Security Managing The Intruder Infosec Resources

Layered Perimeter Protection For Apps Running On Aws Ctd1 R1 Aw

Vpc Service Controls Perimeters And Data Catalog

Senstar Enhancing Razor Wire With Perimeter Intrusion Detection Sensors Senstar

Types Of Perimeter Security Systems Microsegur

Why Traditional Network Perimeter Security No Longer Protects Help Net Security

Comparison Between Three Underground Perimeter Intrusion Detection System Technologies Sensoguard

How To Select The Right Perimeter Sensor To Fit Your Needs
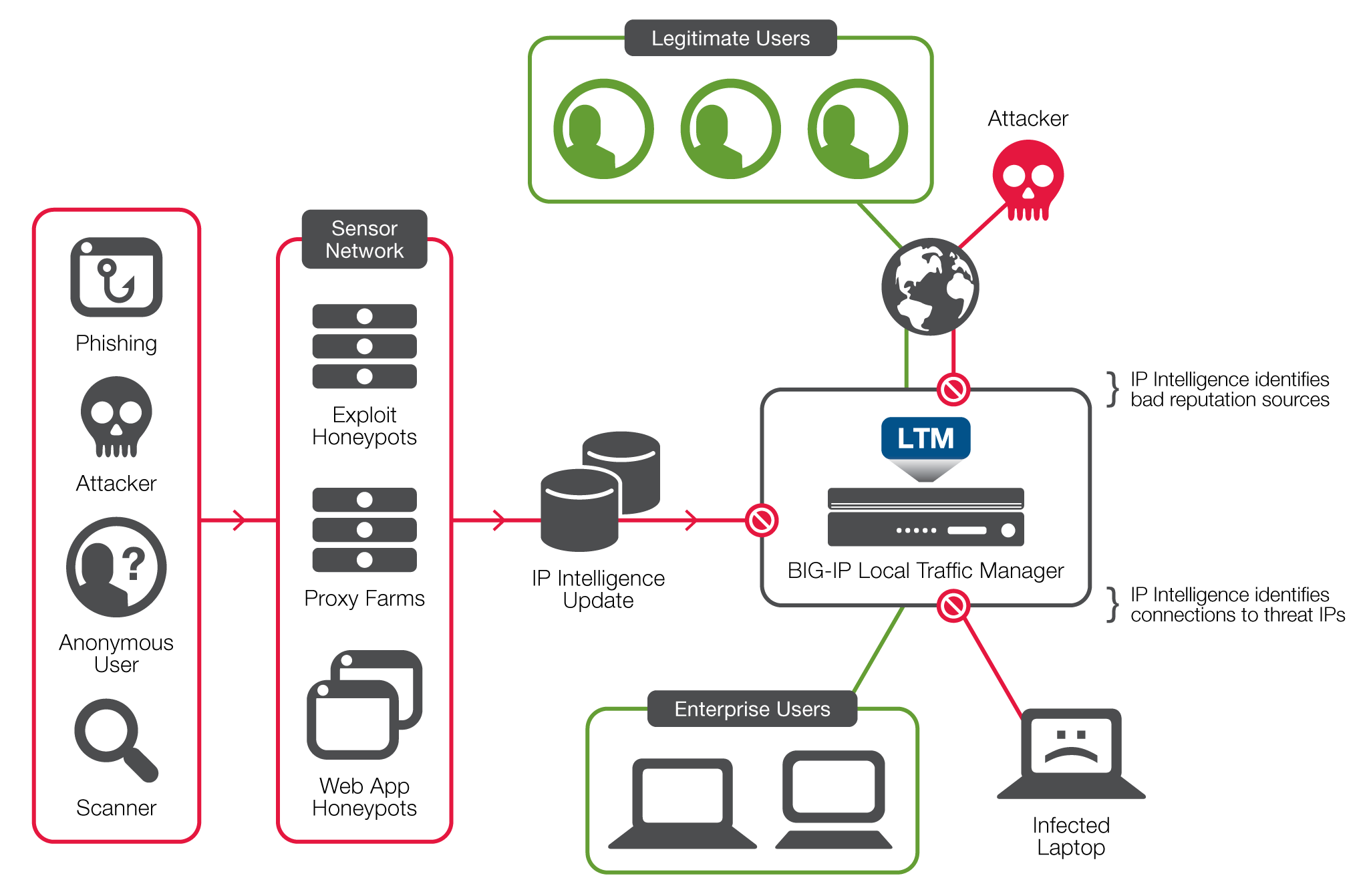
Dynamic Perimeter Security With Ip Intelligence F5

Zero Trust Security What S A Zero Trust Network Cloudflare

The Perimeter Protection Issues Technique And Operation

Types Of Perimeter Security Systems Microsegur

Prison Perimeter Security For Correctional Facilities

Zero Trust Part I The Evolution Of Perimeter Security

Rrs Security Solutions Perimeter Intrusion Monitoring System

Defense In Breadth Or Defense In Depth Cloudnative And Microservices

Dahuawiki

Perimeter Security Protus3

Protective Security Measures For Deter Detect And Delay Beyond The Perimeter Public Website



